SCIM Connector
Introduction
Description
SCIM connector can manage every target system with a published API that allows the SCIM protocol for communication.
SCIM is basically a REST JSON web service with specific HTTP requests and responses, and also a specific JSON format for attributes and values.
For more information about SCIM protocol you could visit its home page: SCIM protocol, or to visit the introduction page of our SCIM addon: Introduction to SCIM
Managed System
The official web of SCIM shows all the possible target systems that allow SCIM protocol: SCIM implementations
Some of the most popular implementations:
- Soffid IAM
- Active Directory SCIM Provisioning
- Oracle Identity Manager
- WSO2 Charo
- Salesforce
- Trello
- Slack
For more information to check if your system may be synchronized with this connector, you do not hesitate to contact us through our Contact form
Prerequisites
t is needed a user with access and permissions to the endpoints and operations required in the scope of the integration.
Also, the documentation, specification or tutorial of the web service, despite SCIM defining a schema for the objects, most applications or servers use to implement extended or customized versions of it.
Download and Install
This addon is located in the Connectors section and its name is SICM connector.
For more information about the installation process, you can visit the Addons Getting started page.
Agent Configuration
Basic
Generic parameters
After the installation of the addon, you may create and configure agent instances.
To configure this SCIM Connector you must select "SCIM" in the attribute "Type" of the generic parameters section in the agents page configuration.
For more information about how you may configure the generic parameters of the agent, see the following link: Agents configuration
Custom parameters
Below there are the specific parameters for this agent implementation:
|
Parameter |
Description |
|---|---|
|
Server URL |
URL of the SCIM web service. It is used as the basis of the URL mapped to call the operations. |
|
Authentication method |
Options:
|
|
User name |
User to authenticate |
|
Password |
Password of the user to authenticate |
|
Authentication URL |
URL to retrieve the token bearer used to authenticate with the "Server URL" |
|
Enable debug |
Two options: "Yes", "No": it enables or not more log traces in the Synchronization Server log |
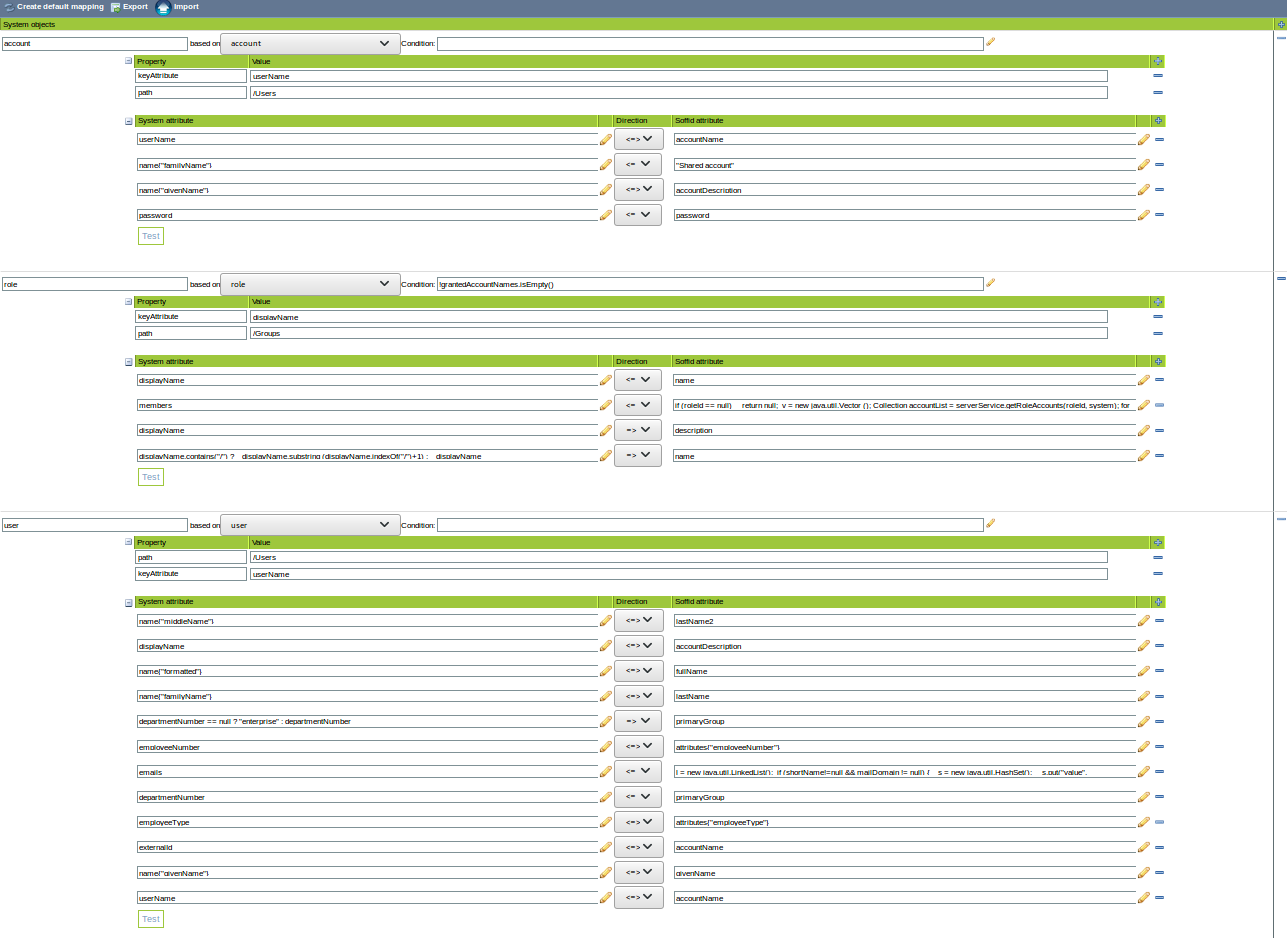
Attribute mapping
This connector can manage users and groups.
Properties
The following properties are defined for each object type:
|
Property |
Meaning |
|---|---|
|
path (required) |
Path relative to main service URL where this type of object is to be managed |
|
keyAttribute (required) |
The SCIM attribute is used to find objects on SCIM repository |
|
changeProperty (optional) |
For authoritative identity sources that support delta changes, this property sets the SCIM attribute used to identify the change number of any object |
|
preventDeletion (optional) |
Set to true to prevent Soffid from removing objects |
Attributes
You may map the attributes of the target system with the Soffid available attributes.
- For the target system attributes are required to be access to its specification
- For the Soffid attributes, you may follow the next link
For more information about how you may configure attribute mapping, see the following link: Soffid Attribute Mapping Reference
If you are trying to connect to WSO2IS server, you must enable the WSO2 workaround setting, in order to bypass some WSO2 buggy implementations. You can get default mappings for WSO2IS here: wso2is-config.xml. Download it and import it into the Soffid agent attribute mappings form.
For example:
Triggers
Load triggers
Account metadata
Agents allow you to create additional data, on the "Account metadata" tab, to customize the accounts created for that agent. This additional information will be loaded with the agent's information, or calculated as defined in the mappings.
The additional data can be used in both mappings and triggers.
The attributes which you define here will be shown when you click on the proper account, on the Accounts Tabs on the users' page.
Operational
Monitoring
After the agent configuration you could check on the monitoring page if the service is running in the Synchronization Server, please go to:
Tasks
Authoritative
If you are checked "Authorized identity source", an automatic task to load identities from the managed system to Soffid is available, please go to:
And you will something like "Import authoritative data from <AGENT_NAME>".
Reconcile
If you are configured the "Attribute Mapping" tab with some of our objects: "user, account, role, group or grant", an automatic task to synchronize these objects from the managed system to Soffid is available, please go to:
And you will do something like "Reconcile all accounts from <AGENT_NAME>".
Synchronization
Regarding the synchronization of the objects, there are two possible options:
- If you are checked the generic attribute "Read Only" in the "Basics" tab, only the changes in the managed systems will be updated in Soffid. We recommend these options until the global configuration of Soffid will be tested.
- If you are not checked the generic attribute "Read Only" in the "Basics" tab, all the changes in Soffid or the managed system will be updated in the other. Note that this synchronization must be configured in the "Attribute mapping" tab correctly.
For more information about how you may configure the generic parameters of the agent, see the following link: Agents configuration