Openid-connect to SAML interoperability
Introduction
OpenID-Connect has a clear design suitable for both frontend and backend.
SAML has a clear design for the frontend, but the backend usage is harder as the security in SAML cannot be placed at transport layer. Instead, in must be placed at document level. Additionally, it requires intensive use of cryptographic algorithms for signature and encryption.
That’s why some applications put a SAML frontend protection for both the frontend and relay on the session cookies generated by the fronted for backend access.
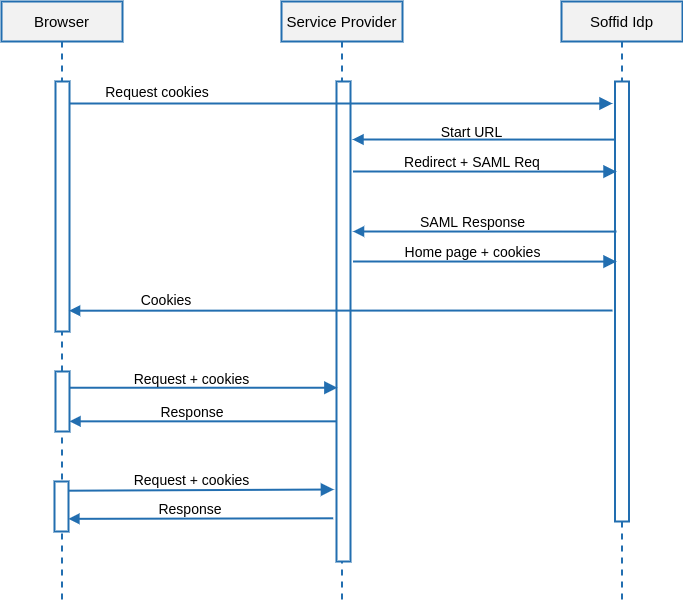
The problem arises when one service provider needs to invoke some services from a SAML enabled application that does not support or implement WS-Security.
To solve it, Soffid Identity Provider provides a service to get the session cookies required to access to a SAML application.
Architecture
The rest service /userinfo/impersonate?url=…. will do the job, and will return the cookies to use to act upon the target application impersonating the current user.
Request
|
POST https://<YOUR_SERVER>:2443/userinfo/impersonate?url=http://targetapplication/ [ } |
Parameters
- URL: is the access URL for the target application.
- Authorization: contains the oauth token.
Response
The response contains the list of cookies to send to the target application.
|
[ } |
Request
Once the application has got the list of cookies, it can invoke the target application URL
|
POST https://targetapplication/api/service1 |
As security measures, the impersonation profile must be enabled, and the source application must be entitled to use it against the target application
