Implementation Report
This report summarizes how Soffid has been implemented for this project.
Agents
These agents have been defined in Main Menu > Administration > Configuration > Integration engine > Agents:
1. IdP Agent
This agent has been created for the identity provider, for managing and authenticating the identities of users. It would be linked to the identity provider through its Public ID.
2. Source AD Agent
This agent has been created to connect the Soffid console with the Active Directory, so we can carry out the authoritative load, to retrieve identities, and the reconciliation process, to request the accounts and ensure that all users are aligned with their respective roles and responsibilities.
Identity & Service providers
Only one Entity Group has been defined (Postbank) in Main Menu > Administration > Configuration > Web SSO > Identity & Service providers. The providers defined within this group are:
1. Identity Providers
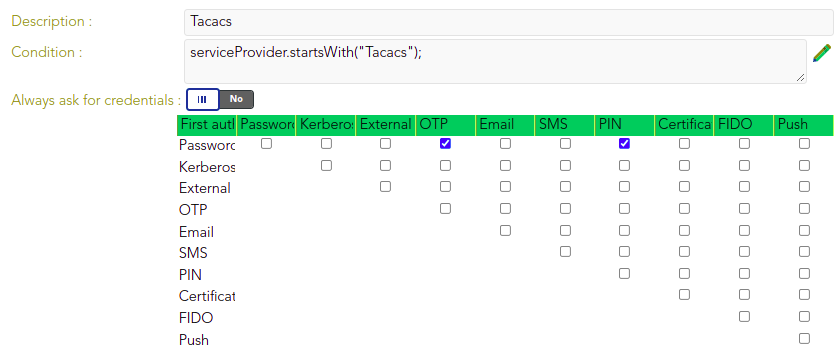
The identity provider uses Soffid IdP for identity authentication. Adaptive authentication is configured, so if the name of the service provider requesting authentication begins with "Tacacs," two-factor authentication (2FA) will be required, as shown below.
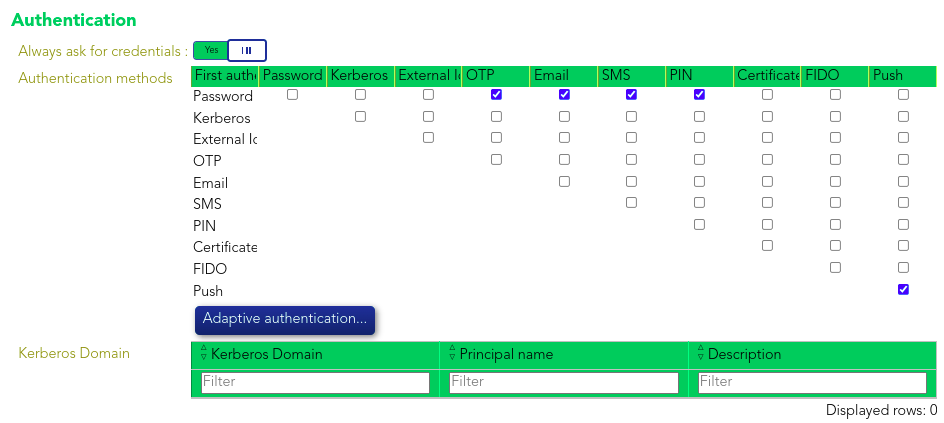
Otherwise multi-factor authentication (MFA) will be required.
2. Service Providers
Some service providers which grant access to firewalls, routers and other systems, are prefixed with "Tacacs", thus 2FA will be required. For the remaining service providers, which allow access to proxies and other systems, MFA will be enforced. These providers enable users to connect to various systems directly, without initiating the connection through Soffid, while still ensuring identity authentication through the identity provider.
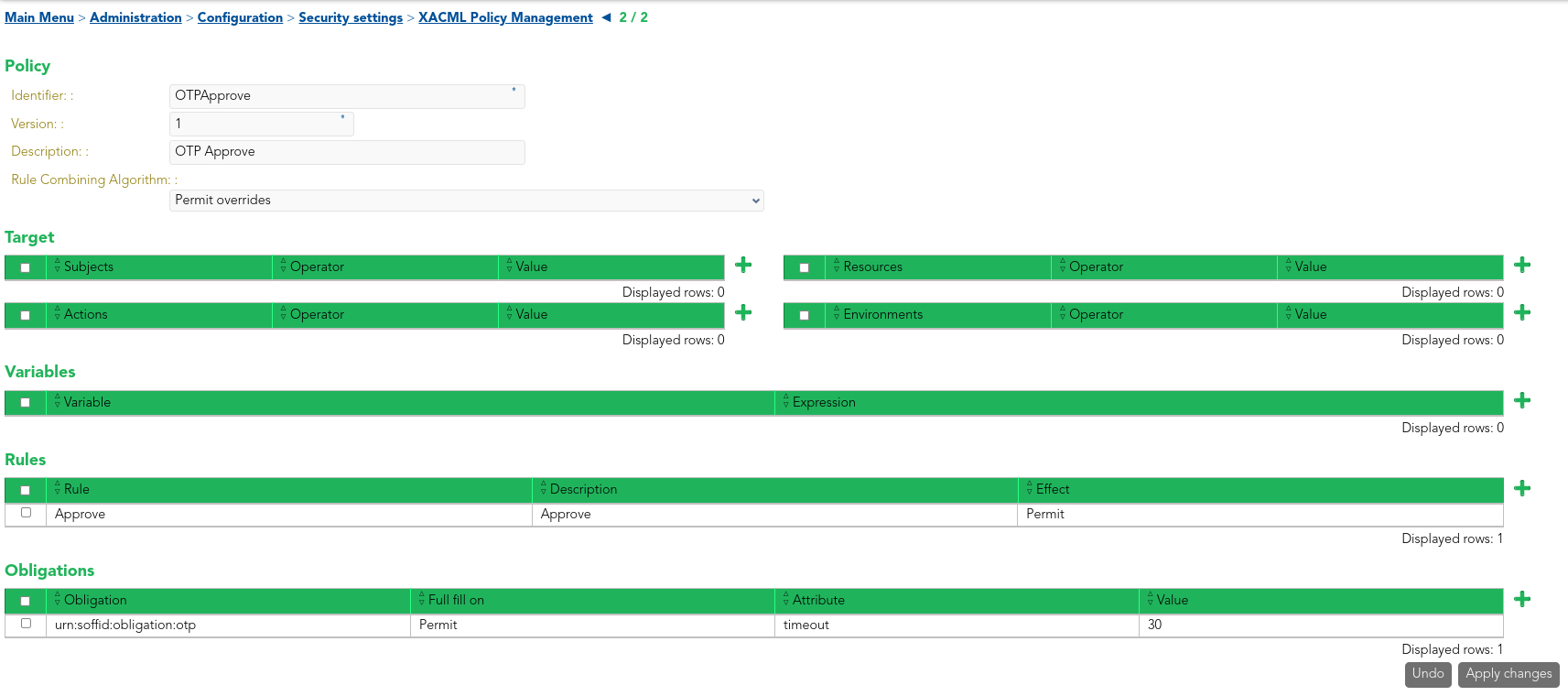
XACML Policy Management
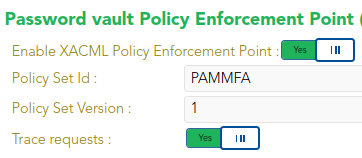
This policy is enabled through the Password vault Policy Enforcement Point in Main Menu > Administration > Configuration > Security Settings > XACML PEP configuration, where the Policy Set Id and the Policy Set Version must be specified.
Password Vault