Implementation
This document summarizes how Soffid has been implemented for this project.
Agents
TheseThe following agents are definedconfigured inunder Main Menu > Administration > Configuration > Integration engine > Agents:
1. IdP Agent
This agent hasis been created for the identity provider,responsible for managing user authentication and authenticatingidentity validation. It is integrated with the identitiesIdentity ofProvider users.(IdP) It would beand linked to theit identity provider throughusing its Public IDID, ensuring seamless communication for identity verification and user access.
2. Source AD Agent
ThisThe agentSource hasAD beenAgent created to connectconnects the Soffid console with the Active Directory,Directory (AD) to manage user data and synchronization, so we can carry out the authoritative load, to retrieve identities, and the reconciliation process, to request the accounts and ensure that all users are aligned with their respective roles and responsibilities.
3. SSO Agent
Additionally, theThe SSO Agent hasis been createdresponsible for managing user login sessionssession across applications,multiple allowingapplications. usersThis toagent authenticateserves once.as an auxiliary component that facilitates the registration of local accounts in the password vault. This capability allows for secure storage and management of user credentials.
For more information, please refer to Agents.
Web SSO
To enable access to multiple applications with a single login, Web Single SIgn-Sign-On (WSSO) is used.utilized. The following elements are required for thisits purpose we need to define:configuration:
1. Attribute definition
2. Attribute definitionsharing policies
3. Identity & Service Providers
Only one Entity Group has been created (Postbank) in Main Menu > Administration > Configuration > Web SSO > Identity & Service providers. The providers defined within this group are:
3.1. Identity Providers
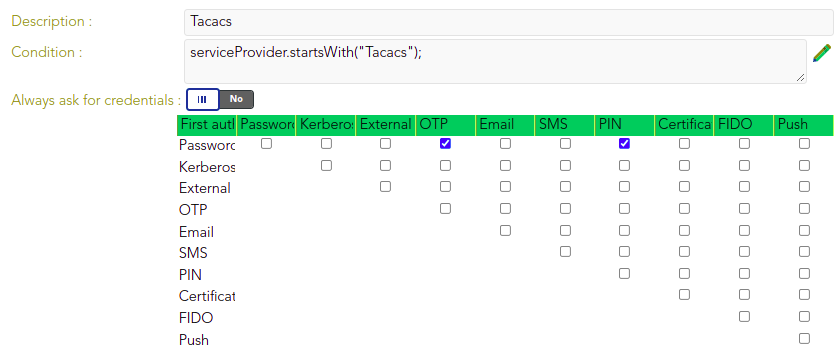
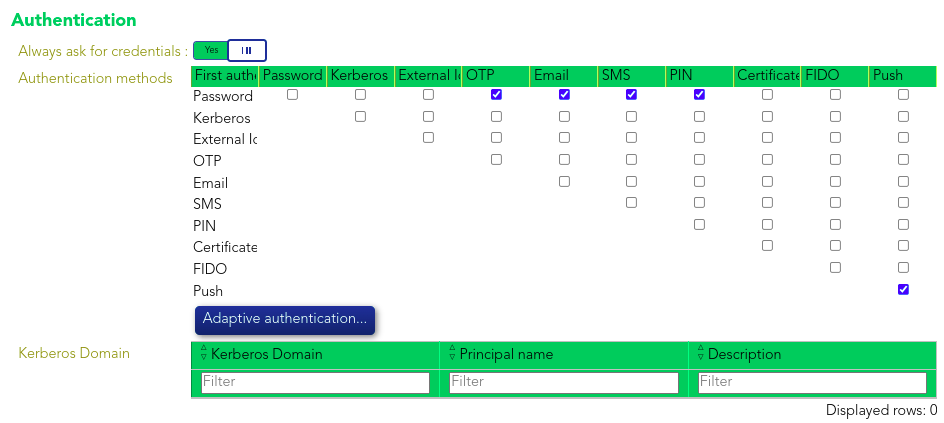
The identity provider uses Soffid IdP for identity authentication. Adaptive authentication is configured, so if the name of the service provider requesting authentication begins with "Tacacs,"Tacacs", it indicates that the service provider is utilizing the Terminal Access Controller Access-Control System (TACACS) and two-factor authentication (2FA) will be required, as shown below.
Otherwise multi-factor authentication (MFA) will be required.
Additionally, TLS and SAML can be configured using certificates and private keys, uploading the PKCS12 files which have already been uploaded.
3.2. Service Providers
Some service providers which grant access to firewalls, routers and other systems, are prefixed with "Tacacs", thus 2FA will be required. For the remaining service providers, which allow access to proxies and other systems, MFA will be enforced, as stated previously. These providers allow users to connect to various systems directly, without initiating the connection through Soffid, while still ensuring identity authentication through the identity provider.
For more information, please refer to IdentityWeb & Service ProvidersSSO..
XACMLPassword Policy ManagementVault
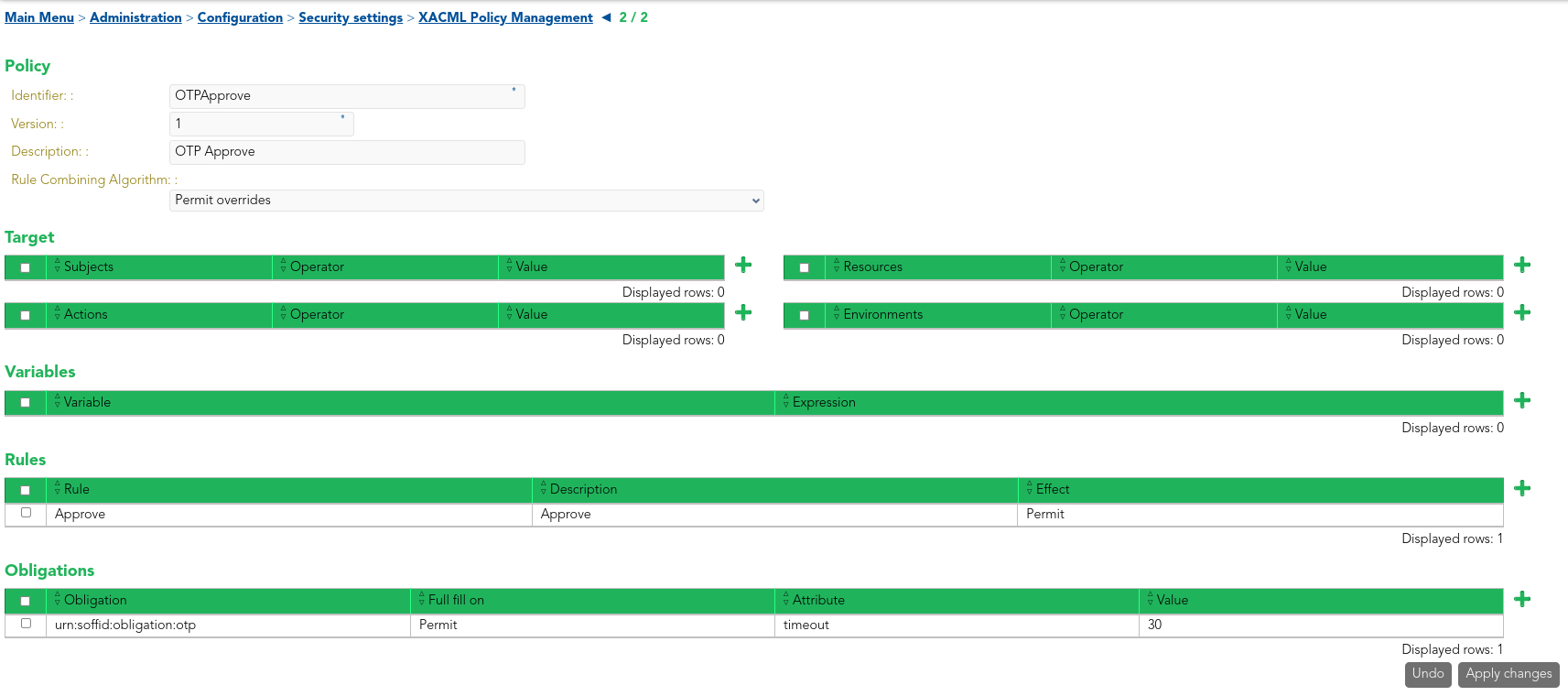
InAs an example, in Main Menu > Administration > the ConfigurationResources > SecurityPassword Settings > XACML Policy ManagementvaultpolicyPAM setTests PAMMFAfolder has been created, within which thetwo policyaccounts OTPApprove hashave been defined.created Itaswell.
1. thePAM obligationTEST RDP
This account allows us to request an OTP with a timeout when launchinglaunch a connection to a machine through PAM.the PAM Launcher of Soffid. For this purpose, in "Basics", it is mandatory to indicate the login URL, where the network protocol must be specified (RDP in this case), together with the IP of the machine that we want to connect to. We also need to specify the Launch type, indicating it is a PAM Jump Server, and the Jump server group corresponding to the PAM Jump Server. Additionally, owners can be selected to handle privileged access.
Thisin policy"Actions", isa enabledpassword throughmust be set in the Password"Set vaultnow" Policyoption, Enforcementso Pointwe can launch the connection and unlock the use of the account. Have in mind that we can change the password policies in Main Menu > Administration > Configuration > Security Settings > XACMLPassword PEP configurationPolicies,. whereHowever, when launching the Policyconnection Setan IdOTP andwill be requested, due to the PolicyPassword Setvault Versionpolicy mustpreviously beexplained. specified.
2. PAM TEST SSH
For more information, please refer to XACMLPassword Policy Management and XACML PEP configurationvault.
Password Vault
As an example, in Main Menu > Administration > Resources > Password vault the PAM Tests folder has been created, within which two accounts have been created aswell.
1. PAM TEST RDP
This account allows us to launch a connection to a machine through the PAM Launcher of Soffid. For this purpose, in "Basics", it is mandatory to indicate the login URL, where the network protocol must be specified (RDP in this case), together with the IP of the machine that we want to connect to. We also need to specify the Launch type, indicating it is a PAM Jump Server, and the Jump server group corresponding to the PAM Jump Server. Additionally, owners can be selected to handle privileged access.
Consequently, in "Actions", a password must be set in the "Set now" option, so we can launch the connection and unlock the use of the account. Have in mind that we can change the password policies in Main Menu > Administration > Configuration > Security Settings > Password Policies. However, when launching the connection an OTP will be requested, due to the Password vault policy previously explained.
2. PAM TEST SSH
Another account has been defined for launching a connection through SSH. The concepts explained in the previous account extend to this one.
For more information, please refer to Password vault.
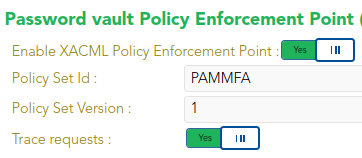
XACML Policy Management
This policy is enabled through the Password vault Policy Enforcement Point in Main Menu > Administration > Configuration > Security Settings > XACML PEP configuration, where the Policy Set Id and the Policy Set Version must be specified.
For more information, please refer to XACML Policy Management and XACML PEP configuration.
Connectors
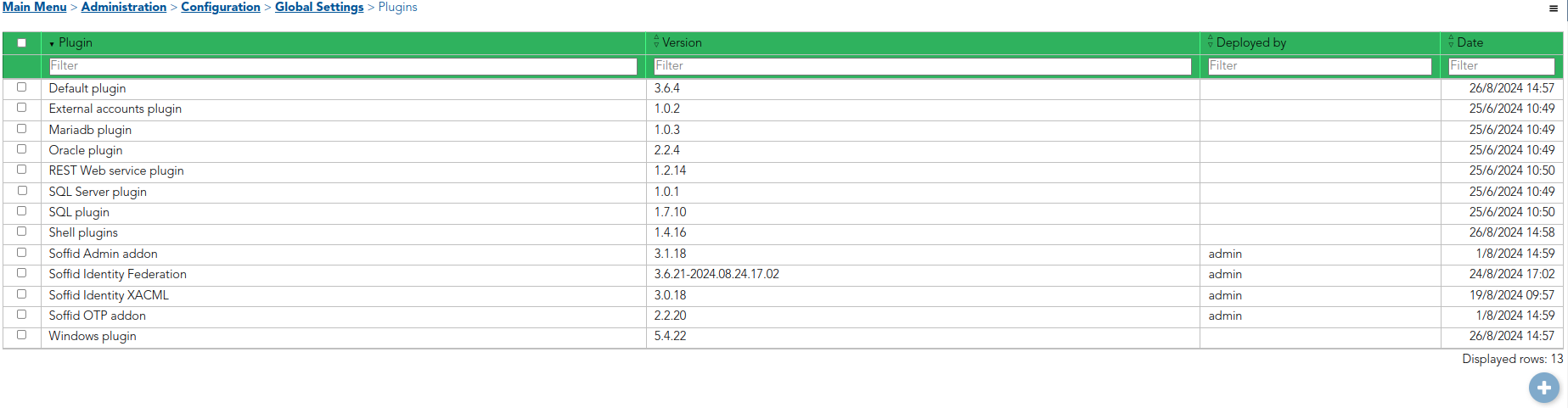
The plugins required for the connectors are stored in Main Menu > Administration > Configuration > Global Settings > Plugins, where the addon files can be uploaded.
These tools help manage external accounts, databases like MariaDB, Oracle, and SQL Server, and interact with REST web services. They also provide SQL execution capabilities, shell scripting, and seamless integration with Windows environments. On the security and identity management side, we have connectors that handle identity federation, XACML and multi-factor authentication via OTP.
For more information, please refer to Connectors.