SAML2ECPProfile
Definition
The enhancedEnhanced clientClient profileProfile is used when the Service Provider is not a web application. Nowadays, it is rarely used, as most mobile applications have shifted to OAuth or OpenIDConnect.
Screen overview
1 &&TODO&& se repite sign assertion, la segunda es sign Requests
2 &&TODO&& En encrypt assertions no hay lista desplegable
3 &&TODO&& ¿Que ocurre si selecciono la opcion en blanco? ¿cómo se comportaría?
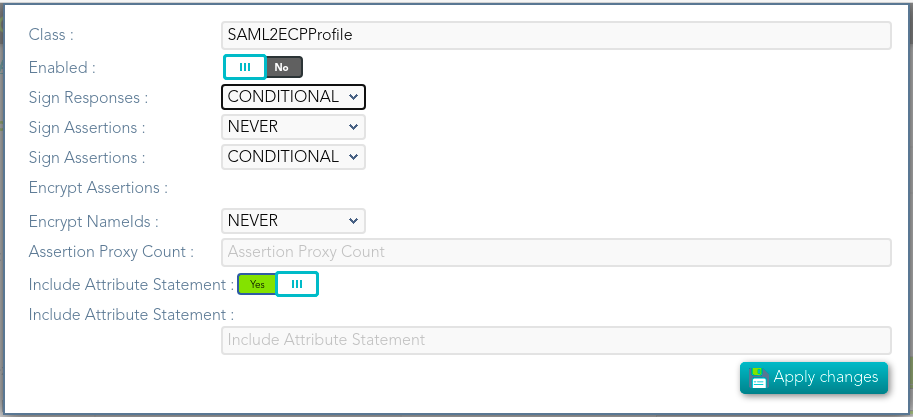
Standard attributes
- Class: class
name.name (readOnly field). - Enabled: if it is checked (selected option is Yes) that protocol will be
enabled.enable. - Sign Responses:
ausually it can be set to never, as long as the assertions are signed. Its preferable to signresponseassertionsguaranteesrather than responses, because the assertion can be forwarded by the service providerthatto another service provider, but the responsehas been issued by the Identity Provider&&TODO&&Conditional ¿Como funciona?AlwaysNever
- Sign Assertions: it's advisable to sign every assertion, so it avoids assertion spoofing. The
&&TODO&&assertion can be forwarded by the service provider to another service provider. - Sign
AssertionsRequest:&&TODO&&the identity provider will issue requests to service providers in order to perform the single logout process. Unless it is needed by any service provider, leave it to conditional. - Encrypt Assertions:
it'sis agooddesiredpracticefeature, but some service providers, mainly public cloud service providers do not support it. Thus, the default value is to never encrypt, but you can set it to optional or always as needed.- If you set it to optional and the public key of the service provider who is going to receive the assertion is available, it will be used to encrypt
assertions.it. - If you set it
makestomorenever,dificultit will not ever be encrypted in any case. - If you set it to
diagnosealways,misconfigurationbutoftheSAMLremotefederation.serviceDisableprovideritencryptiononlykeywhenisneeded.unknown, an exception will be raised.
Nevertheless, - If you set it to optional and the public key of the service provider who is going to receive the assertion is available, it will be used to encrypt
- Encrypt NameIds:
encryptshouldNamebeIdsletwhentothey are not part of an assertion.never. - Assertion Proxy Count: sets the maximum number of
SAML proxieshops that canforwardbeanaccepted for any assertion. A number of 0standsdoesfornotnosetlimit.any limit - Include Attribute Statement:
on- If
SSOattributeprofilestatementswillaregivenot included (selected value is No), the service providereverywill receive the SAML assertion with the principal name, then the service provider will issue a attributeboundstatement request to theidentifiedserviceuser,provideravoidto get them. - If the
need for extraattributerequests.statements- are
IncludeincludedAttribute(selectedStatementvalue:is&&TODO&&Yes),estetheesperformanceuniscampoincreaseddeastextothisdebajoadditionaldelstepcheckisanteriorno longer needed. It is particularly recommended when using public cloud service providers.
LocalityIncludeDNSAttributeNameStatement: &&TODO&&
a - If
