External oAuth / OpenID Identity Providers
Introduction
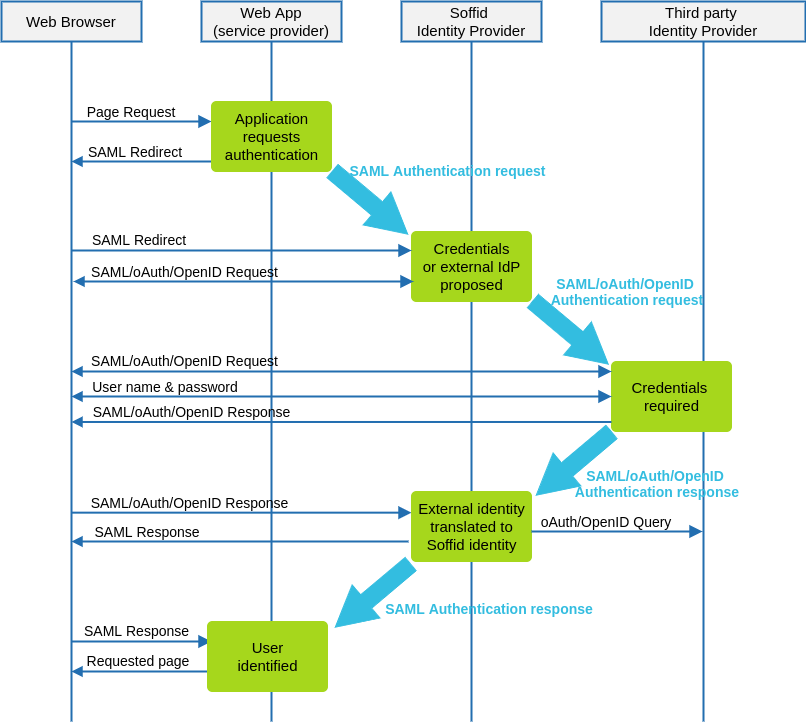
An Identity Broker is often part of a a Single Sign-On Architecture as an an intermediary service that connects multiple Service Providers with different Identity Provider (IDP)s.
Soffid IdPfederation can actbe ascomposed anby identitya broker.mix Thisof meansSAML thatand oAuth / OpenID-connect servers. In such a scenario, Soffid IdP canis rely on third party identity providersable to identifylet users.users be identified by oAuth servers like Linked-in, Google or Facebook, perform all the provision tasks required and send back a SAML assertion to the service provider requiring user authentication.
To act ascreate an external oAuth identity broker,provider, you can choose the ExternalIdp SAMLtype identityfrom providera optionlist mustof bepopular enabledsites, onlike theGoogle Authenticationor page.Facebook, Youor canwrite visityou theown Authentication page for more info.descriptor.
Data flow
The followingdescriptor diagram,should showsfollow the resultingOpenID dataconnect flowdiscovery betweenJSON document. Most parameters are optional, but these are required:
7.1.Next, Foryou OpenID-Connectmust responses,register Soffid IdP with your oAuth server. After registering, you will get a oAuthKey (some kind of username) and an oAuthSecret (some kind of password). To register Soffid IdP, your oAuth server will require you to specify the redirection endpoint. This redirection endpoint refers to your Soffid IdP and will receive the authorization token generated by the oAuth server.
If your Soffid IdP is usedlistening to https://idp.yourdomain.com:2443/, your redirection endpoint will be https://idp.yourdomain.com:2443/oauthResponse
As an example, here you have some links to get ayour sessionoAuth token along the OpenID token received. The OpenID token is parsed as a JWT token,keys and eachsecrets claimed attribute is parsed.
8. Soffid IdP finds the identity owner of the external identity. If no identity is found, depending on Soffid IdP configuration, it can automatically create a Soffid Identity based on received attributes.
9. Finally, Soffid IdP issues a SAML assertion containing Soffid identity attributes.for Google, Facebook and Linkedin.