# XACML
# Introduction to XACML
## What is XACML?
XACML "eXtensible Access Control Markup Language" is an open standard XML based language. The standard defines a declarative fine-grained, attribute-based access control policy language, an architecture, and a processing model describing how to evaluate access requests according to the rules defined in policies. (\*)
**XACML policy language**: is used to describe general access control requirements
**XACML request/response protocol**: used to query a decisioning engine that evaluates real-world access requests against existing XACML policies.
**XACML reference architecture**: provides a standard for the deployment of necessary software modules to achieve efficient enforcement of XACML policies.
## Terminology
- **PAP - Policy Administration**: Point Point which manages access authorization policies.
- **PDP - Policy Decision Point**: Point which evaluates access requests against authorization policies before issuing access decisions.
- **PEP - Policy Enforcement Point**: Point which intercepts the user's access request to a resource, makes a decision request to the PDP to obtain the access decision
- **PIP - Policy Information Point**: It is the system entity that acts as the source of attribute values. It provides additional information about the attributes needed by the **PDP (Policy Decision Point)** to make authorization decisions.
- **PRP - Policy Retrieval Point**: Point where the XACML access authorization policies are stored, typically a database or the filesystem.
*(\*) Wikipedia definition*
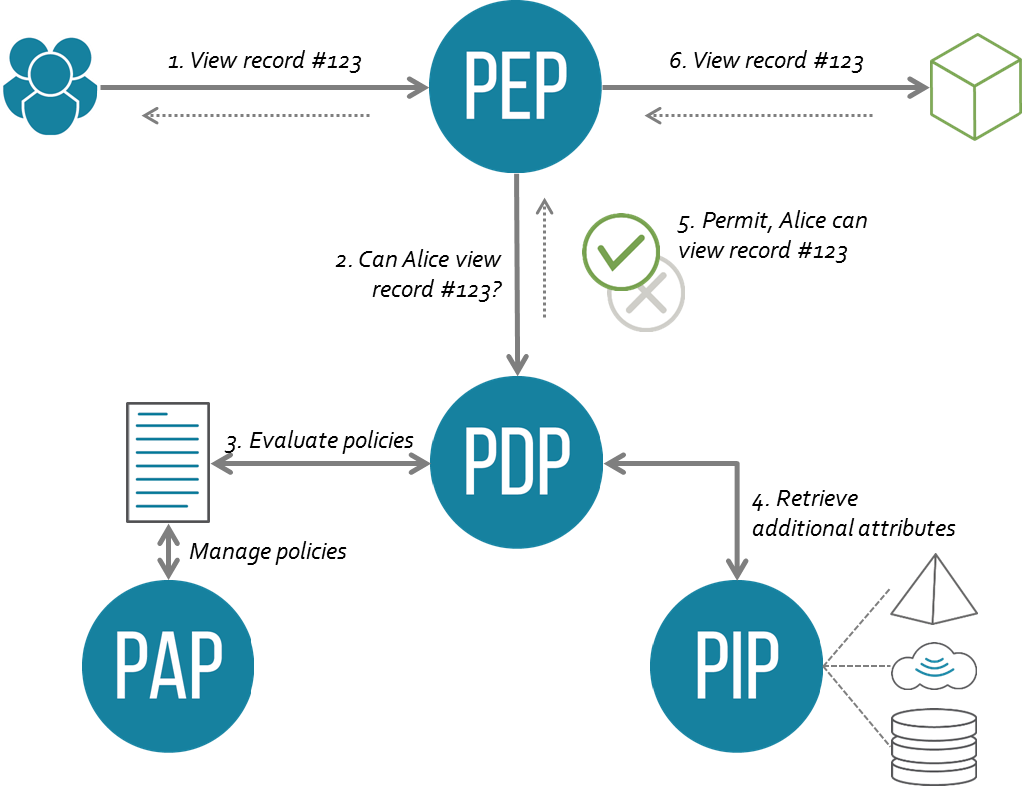
## Flow
1. A user sends a request which is intercepted by the Policy Enforcement Point (PEP).
2. The PEP converts the request into a XACML authorization request and forwards the authorization request to the Policy Decision Point (PDP).
3. The PDP evaluates the authorization request against the policies it is configured with. The policies are. acquired via the Policy Retrieval Point (PRP) and managed by the Policy Administration Point (PAP).
4. If needed it also retrieves attribute values from underlying Policy Information Points (PIP).
5. The PDP reaches a decision (Permit / Deny / NotApplicable / Indeterminate) and returns it to the PEP.
[](https://bookstack.soffid.com/uploads/images/gallery/2021-07/image-1627459612625.png)
*(\*) Wikipedia definition*
In Soffid, PAP and PIP are implemented on the Console.
## Soffid XACML
Using the XACML addon it is possible to add access controls XACML standard to the Soffid console. In this case, Soffid can be able to add more complex and restricted rules to the authorizations.
---
*(\*) [https://en.wikipedia.org/wiki/XACML](https://en.wikipedia.org/wiki/XACML)*
*(\*\*) [https://www.oasis-open.org/committees/tc\_home.php?wg\_abbrev=xacml#XACML20](https://www.oasis-open.org/committees/tc_home.php?wg_abbrev=xacml#XACML20)*
[*https://docs.oasis-open.org/xacml/2.0/access\_control-xacml-2.0-core-spec-os.pdf*](https://docs.oasis-open.org/xacml/2.0/access_control-xacml-2.0-core-spec-os.pdf)
# How to install XACML in Soffid
## Installation
### Download
Please download the Soffid XACML add-on.
You can download it at the following link [http://www.soffid.com/download/enterprise/](http://www.soffid.com/download/enterprise/) if you have Soffid user with authorization, or in the following [http://download.soffid.com/download/](http://download.soffid.com/download/) by registering.
### Upload
Once the XACML add-on is downloaded, please log in to IAM Console.
You need to be an administrator user of the Soffid console or a user with permissions to upload addons.
It is recommended to upload the addons to master, this is the way to maintain updated all, master and tenants if there are.
In the Soffid console, please go to: "Main Menu > Administration > Configure Soffid > Global Settings > Plugins" and upload the addon file, for more information visit the [Addons Getting started](https://bookstack.soffid.com/books/addons-getting-started/page/getting-started "Addons installation") page
Finally, when the addon is installed, it will be required to restart the Soffid Console.
# Policy Enforcement Point (PEP)
## Description
The **PEP, Policy enforcement point**, is a component of policy-based management, **where enforce the policies**. It is the component that serves as the gatekeeper to access a digital resource. The PEP gives the PDP, Policy Decision Point, the job of deciding whether or not to authorize the user based on the description of the user's attributes.
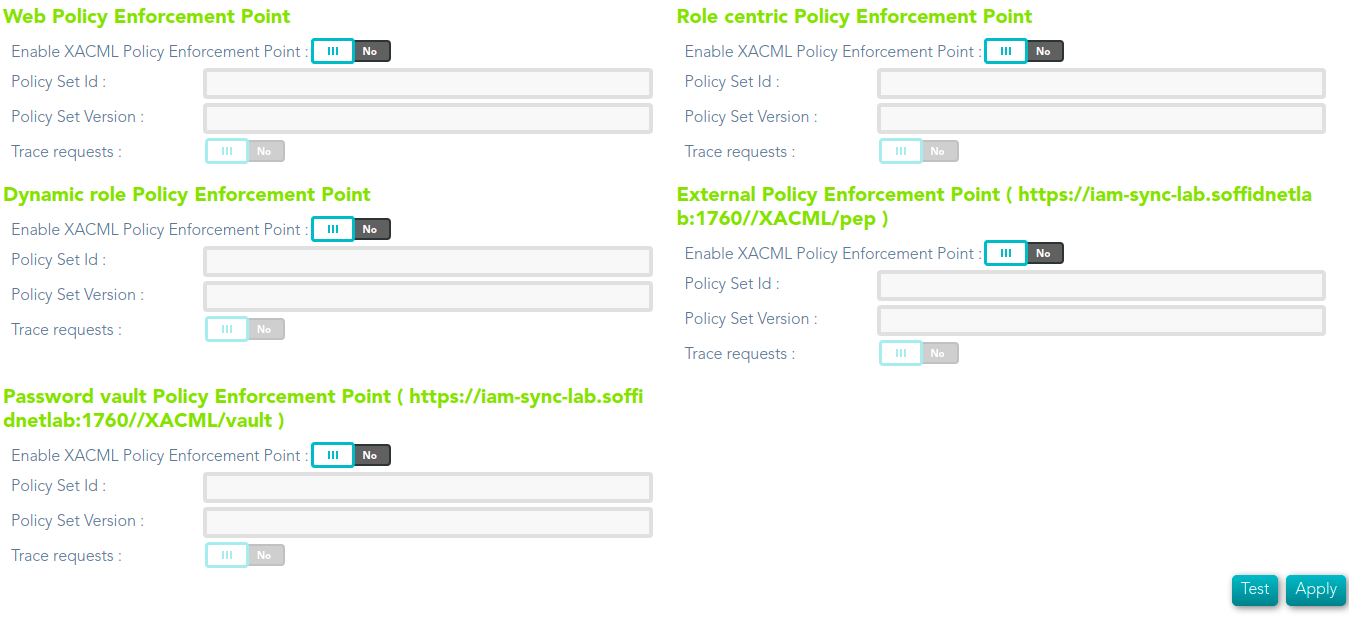
## XACML PEP configuration
Soffid allows you to configure different policies enforcement points, each of then can use a different policy set.
`Main Menu > Administration > Configuration > Security settings > XACML PEP configuration`
- [Web Policy Enforcement Point](#bkmrk-web-policy-enforceme-1)
- [Role centric Policy Enforcement Point](#bkmrk-role-centric-policy-)
- [Dynamic role Policy Enforcement Point](#bkmrk-dynamic-role-policy-)
- [External Policy Enforcement Point](#bkmrk-external-policy-enfo)
- [Password vault Policy Enforcement Point](#bkmrk-password-vault-polic)
## Screen
[](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628231580976.png)
## Common attributes
Common attributes for each PEP:
- **Enable XACML Policy Enforcement Point**: select the Yes option to enable the PEP.
- **Policy Set Id**: policy set identifier.
- **Policy Set Version**: version of the policy set to enforce.
- **Trace requests**: select the Yes option to enable the trace.
## Policies enforcement points
### Web Policy Enforcement Point
The policy will be enforced when the user open a new Soffid page. Using this PEP you can define the rules to access to Soffid pages.
| **SUBJECTS** | **RESOURCES** | **ACTIONS** | **ENVIRONMENTS** |
| User
User attributes
Account
System
Role
Group
Primary Gorup
IP Address
| Server URL | Get
Put
Post
| Current Time
Current Date
Current DateTime
|
### Role centric Policy Enforcement Point
The policy will be enforced when the user login into Soffid. It will calculate the user authorizations as of the permissions that the user has assigned.
| **SUBJECTS** | **RESOURCES** | **ACTIONS** | **ENVIRONMENTS** |
| User
User attributes
Account
System
Role
Group
Primary Gorup
IP Address
| Soffid object
Attributes
| create
update
delete
query
| Current Time
Current Date
Current DateTime
|
### Dynamic role Policy Enforcement Point
The policy will be enforced when the user performs an action to evaluate if the user has or not authorization. The user must have the proper role and comply with the XACML rule.
You can use that PEP to split the permissions, for instance, a support group can update the permission of a specific group of user, and another support group can update the permissions of another group of users.
| **SUBJECTS** | **RESOURCES** | **ACTIONS** | **ENVIRONMENTS** |
| User
User attributes
Account
System
Role
Group
Primary Gorup
IP Address
| Soffid object
Attributes
(\*)
| create
update
delete
query
| Current Time
Current Date
Current DateTime
|
(\*) It is allowed to use "Attribute Selector" to configure Dynamic role policy.
### External Policy Enforcement Point (https://iam-sync-lab.soffidnetlab:1760//XACML/pep)
PEP of general purpose. Calling the web service, the clients can made validations and figure out if the users have access.
| **SUBJECTS** | **RESOURCES** | **ACTIONS** | **ENVIRONMENTS** |
| User
User attributes
Account
System
Role
Group
Primary Gorup
IP Address
| Token
Method
Soffid object
| Get
Put
| Current Time
Current Date
Current DateTime
|
### Password vault Policy Enforcement Point (https://iam-sync-lab.soffidnetlab:1760//XACML/vault)
The policy will be enforced when the password vault is used.
| **SUBJECTS** | **RESOURCES** | **ACTIONS** | **ENVIRONMENTS** |
| User
User attributes
Account
System
Role
Group
Primary Gorup
IP Address
| Access level
Account
System
Login
Vault Folder
Server URL
| setPassword
queryPassword
queryPasswordBypassPolicy
launch
| Current Time
Current Date
Current DateTime
|
# Policy Decision Point (PDP)
## Definition
The **PDP, Policy Decision Point**, is in charge of evaluating the defined rules. The Policy Decision Point is essentially a policy compiler. The PDP must verify that the specified rules are within the scope of the rule authors authority. The PDP **provides the authorization** to the PEP.
## XACML Policy Management
The policy language is used to describe general access control requirements, and has standard extension points for defining new functions, data types, combining logic, etc. The request/response language lets you form a query to ask whether or not a given action should be allowed, and interpret the result.
`Main Menu > Administration > Configuration > Security settings > XACML Policy Management`
It is possible to import an existing PolicySet into Soffid. The file to import must be a well-formed XML.
To know more about XACML, read [XACML 2.0 Standard Specification](https://www.oasis-open.org/committees/tc_home.php?wg_abbrev=xacml#XACML20)
## Related objects
- [Policy set](https://bookstack.soffid.com/books/xacml/page/policy-set "Policy set")
- [Policy](https://bookstack.soffid.com/books/xacml/page/policy "Policy")
- [Policy set reference](https://bookstack.soffid.com/books/xacml/page/policy-set-reference "Policy set reference")
- [Policy reference](https://bookstack.soffid.com/books/xacml/page/policy-reference "Policy reference")
---
*[https://www.oasis-open.org/committees/download.php/2713/Brief\_Introduction\_to\_XACML.html](https://www.oasis-open.org/committees/download.php/2713/Brief_Introduction_to_XACML.html)*
# XACML Rule combining algorithm
## Definition
> The rule-combining algorithm defines a procedure for arriving at an authorization decision given the individual results of evaluation of a set of rules
XACML rule combining algorithms is in charge to combine the decisions produced by different children of a parent policy (or policy set) into a single decision.
## Policies
Soffid has implemented the following Policies:
### Deny overrides
The deny orverrides algorithm is intended for those cases where a deny decision should have priority over a permit decision.
### Permit overrides
The permit overrides algorithm is intended for those cases where a permit decision should have priority over a deny decision.
### First applicable
The first applicable algorithm is intended for evaluate each rule in the order in which is listed in the policy. The algorithm runs through all the rules until in one the target matches and the condition to be evaluated is true. If no further rule in the order exists, then the policy shall evaluate to "NotApplicable".
### Only one applicable
The only one applicable algorithm has three cases:
- If only one policy is applicable, the result will be the result of evaluating the policy.
- If there are not policies applicables the result will be denied.
- If there are more than one policy applicable the result will be denied.
### Ordered deny overrides
The behavior of this algorithm is identical to the Deny overrides policy-combining algorithm with one exception. The order in which the collection of policies is evaluated shal match the order as listed in the policy set.
### Ordered permit overrides
The behavior of this algorithm is identical to the Permit overrides policy-combining algorithm with one exception. The order in which the collection of policies is evaluated shall match the order as listed in the policy set.
---
[*https://docs.oasis-open.org/xacml/2.0/access\_control-xacml-2.0-core-spec-os.pdf*](https://docs.oasis-open.org/xacml/2.0/access_control-xacml-2.0-core-spec-os.pdf)
# Soffid XACML Editor
Soffid XACML Editor
# XACML Editor
## Description
Soffid Console provides a graphical interface, with a hierarchy structure, that allows the management of Policy Decision Points in a easy way. You can create new policy sets, policies, policy set references and policy references.
To start you only need to click the button with the add symbol (+) and start to configure the policy set.
Once you have created the root policy set, you can add new policy sets, polices, policy set references and policy references as your company need. You only need to click on the proper button and fulfill the data. You can add more than one root policy set.
Also, you can import a PolicySet into the system. You need click the import option on the hamburger icon and pick up the file to import, that file must be a well-formed XML.
## Screen overview
## Related objects
- [Policy set](https://bookstack.soffid.com/books/xacml/page/policy-set "Policy set")
- [Policy](https://bookstack.soffid.com/books/xacml/page/policy "Policy")
- [Policy set reference](https://bookstack.soffid.com/books/xacml/page/policy-set-reference "Policy set reference")
- [Policy reference](https://bookstack.soffid.com/books/xacml/page/policy-reference "Policy reference")
## Actions
| **Add new**
| Allows you to add a new policy set. You can choose that option on the hamburger menu or click the add button (+). Second, you need to fulfill the mandatory fields, also the target, and the obligations, and apply changes.
|
| **Import**
| Allows you to import an XML file to add a new policy set. You can choose that option on the hamburger menu. Then you can pick up a .XML file and Soffid will import the file. If you cancel that operation, Soffil will not upload and save the file.
|
| **New policy set**
| Allows you to add a new policy set as a child of another policy set. You can choose that option under the proper policy set, and then fulfill the form.
|
| **New policy**
| Allows you to add a new policy as a child of another policy set. You can choose that option under the proper policy set, and then fulfill the form. |
| **New policy reference**
| Allows you to add a new policy reference as a child of another policy set. You can choose that option under the proper policy set, and then fulfill the form. |
| **New policy set reference**
| Allows you to add a new policy set reference as a child of another policy set. You can choose that option under the proper policy set, and then fulfill the form. |
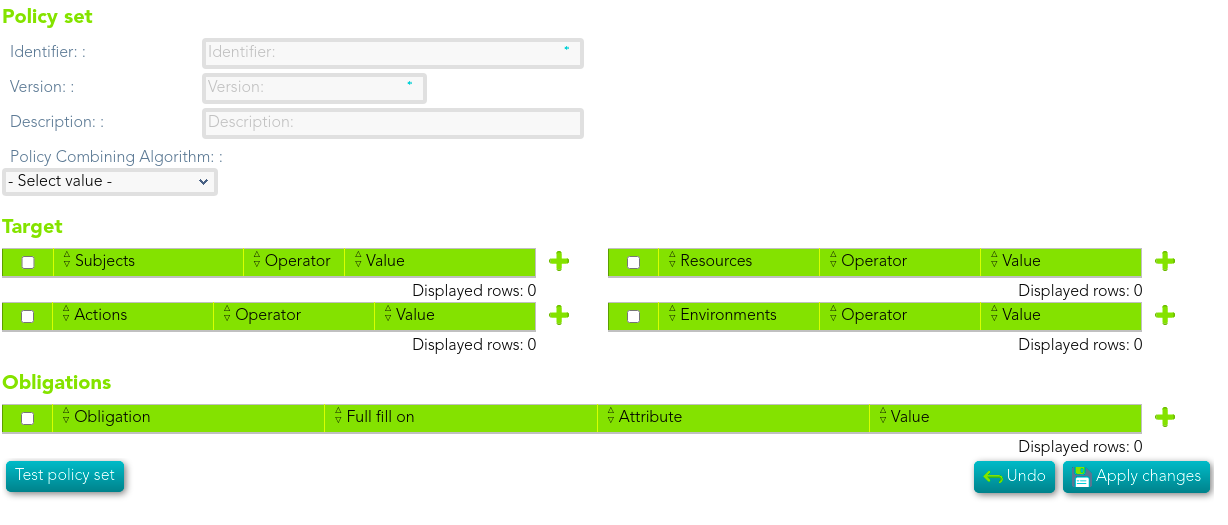
# Policy set
## Description
> A **PolicySet** is a container that can hold other Policies or PolicySets, as well as references to policies found in remote locations.
>
> - Policy Combining Algorithm
> - Target
> - Obligations
Every PolicySet contains a target and obligations, both can be empty.
The target contains the subjects, resources, actions and environments where the policy set will be applied. A target can contain more than one subject, environment, resource or action or none of them.
Policy Set can be exported to an XML file by clicking on Export button. The file will contain the Policy Set Target and all the elements included in it, like other PolicySets, Policies or References.
It is possible to create a new version for a PolicySet by clicking on 'Add new version'. That will copy all PolicySet elements on the tree with the following version number.
## Screen overview
[](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628241289673.png)
## Related objects
- **[Policy](https://bookstack.soffid.com/books/xacml/page/policy "Policy")**
- **[Policy set reference](https://bookstack.soffid.com/books/xacml/page/policy-set-reference "Policy set reference")**
- **[Policy reference](https://bookstack.soffid.com/books/xacml/page/policy-reference "Policy reference")**
- [**Target**](https://bookstack.soffid.com/books/xacml/page/target "Target")
- **[Obligations](https://bookstack.soffid.com/books/xacml/page/obligations "Obligations")**
## Standard attributes
- **Identifier**: identify the policy set.
- **Version**: version of the policy set.
- **Description**: brief description of the policy set.
- **Policy Combining Algorithm:** determines how the different Policies in the PolicySet will be applied. You can visit the [XACML Rule combining algorithm page](https://bookstack.soffid.com/books/xacml/page/xacml-rule-combining-algorithm "XACML Rule combining algorithm") for more information.
- [**Target:**](https://bookstack.soffid.com/books/xacml/page/target "Target") The policy result will be MATCHES if it all the target elements defined match.
- [Subjects](https://bookstack.soffid.com/link/317#bkmrk-subjects)
- [Resources](https://bookstack.soffid.com/link/317#bkmrk-resources)
- [Actions](https://bookstack.soffid.com/link/317#bkmrk-actions)
- [Environments](https://bookstack.soffid.com/Environments)
- **[Obligations](https://bookstack.soffid.com/books/xacml/page/obligations "Obligations")**
## Actions
| **Apply changes**
| Allows you to save the data of a new policy set or to update the data of a specific policy set. To save the data it will be mandatory to fill in the required fields
|
| **Undo**
| Allows you to quit without applying any changes.
|
| **Delete**
| Allows you to delete a policy set. You can choose that option on the trash icon.
To perform that action, Soffid will ask you for confirmation, you could confirm or cancel the operation.
|
| **Export**
| Allows you to export a XML file that contain the policy set.
|
| **Add new version**
| Allows you to add a new versión of the policy set.
|
| **Test policy set**
| Allows you to test the policy set creating the XML file necessary with the defined policies and rules.
|
---
[*https://www.oasis-open.org/committees/download.php/2713/Brief\_Introduction\_to\_XACML.html*](https://www.oasis-open.org/committees/download.php/2713/Brief_Introduction_to_XACML.html)
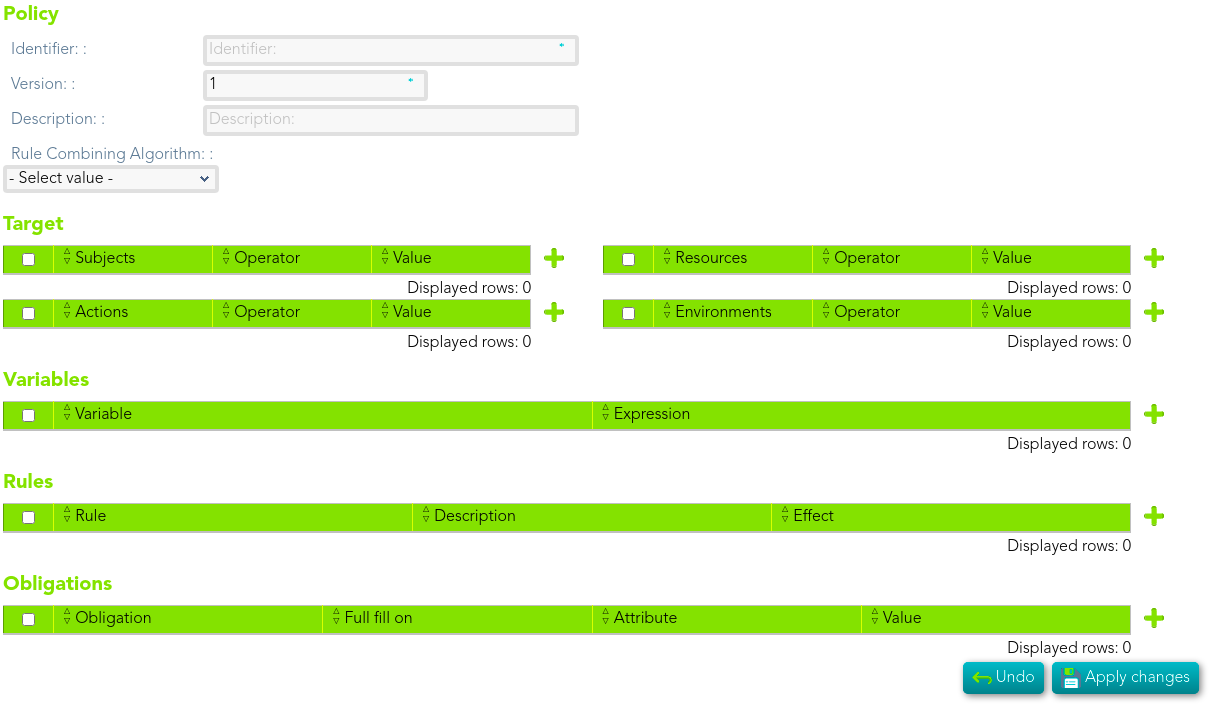
# Policy
## Description
> A Policy represents a single access control policy, expressed through a set of Rules.
>
> - Policy Combining Algorithm
> - Target
> - Variables
> - Rules
> - Obligations
## Screen overview
[](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628241334202.png)
## Related objects
- [**Policy set**](https://bookstack.soffid.com/books/xacml/page/policy-set "Policy set")
- **[Target](https://bookstack.soffid.com/books/xacml/page/target "Target")**
- **[Variables](https://bookstack.soffid.com/books/xacml/page/variables "Variables")**
- **[Rules](https://bookstack.soffid.com/books/xacml/page/rules "Rules")**
- **[Obligations](https://bookstack.soffid.com/books/xacml/page/obligations "Obligations")**
## Standard attributes
### Policy set
- **Identifier**: identify the policy.
- **Version**: version of the policy.
- **Description**: brief description of the policy.
- **Policy Combining Algorithm:** determines how the different rules will be applied. You can visit the [XACML Rule combining algorithm page](https://bookstack.soffid.com/books/xacml/page/xacml-rule-combining-algorithm "XACML Rule combining algorithm") for more information.
### Target
The policy result will be MATCHES if it all the target elements defined match.
- [Subjects](https://bookstack.soffid.com/link/317#bkmrk-subjects)
- [Resources](https://bookstack.soffid.com/link/317#bkmrk-resources)
- [Actions](https://bookstack.soffid.com/link/317#bkmrk-actions)
- [Environments](https://bookstack.soffid.com/Environments)
### Variables
- [Variables](https://bookstack.soffid.com/books/xacml/page/variables "Variables")
### Rules
- [Rules](https://bookstack.soffid.com/books/xacml/page/rules "Rules")
### Obligations
- [Obligations](https://bookstack.soffid.com/books/xacml/page/obligations "Obligations")
## Actions
| **Apply changes**
| Allows you to save the data of a new policy or to update the data of a specific policy. To save the data it will be mandatory to fill in the required fields
|
| **Undo**
| Allows you to quit without applying any changes.
|
| **Delete**
| Allows you to delete a policy. You can choose that option on the trash icon.To perform that action, Soffid will ask you for confirmation, you could confirm or cancel the operation.
|
| **Export**
| Allows you to export a XML file that contain the policy.
|
| **Add new version**
| Allows you to add a new versión of the policy.
|
---
[*https://www.oasis-open.org/committees/download.php/2713/Brief\_Introduction\_to\_XACML.html*](https://www.oasis-open.org/committees/download.php/2713/Brief_Introduction_to_XACML.html)
# Policy reference
## Description
The policy reference is used to reference a policy element. The reference is made by id of the policy. However, the mechanism for resolving a policy set reference to the corresponding policy is outside the scope of this specification.
## Related objects
- [**Policy**](https://bookstack.soffid.com/books/xacml/page/policy "Policy")
## Standard attributes
- **Identifier**: policy set identifier.
- **Version**:
- **Specific version**: specifies a matching expression for the version of the policy referenced
- **Version range**: specifies a range of version
- **Any version**
## Actions
| **Apply changes**
| Allows you to save the data of a new policy reference or to update the data of a specific policy reference. To save the data it will be mandatory to fill in the required fields
|
| **Undo**
| Allows you to quit without applying any changes.
|
| **Delete**
| Allows you to delete a policy reference. You can choose that option on the hamburguer icon. To perform that action, Soffid will ask you for confirmation, you could confirm or cancel the operation.
|
| **Export**
| Allows you to export a XML file that contain the policy reference.
|
| **Add new version**
| Allows you to add a new versión of the policy reference
|
---
*http://docs.oasis-open.org/xacml/2.0/access\_control-xacml-2.0-core-spec-os.pdf*
# Policy set reference
## Description
The policy set reference is used to reference a policy set element. The reference is made by id of the policy set. However, the mechanism for resolving a policy set reference to the corresponding policy set is outside the scope of this specification.
## Related objects
- [**Policy set**](https://bookstack.soffid.com/books/xacml/page/policy-set "Policy set")
## Standard attributes
- **Identifier**: policy set identifier.
- **Version**:
- **Specific version**: specifies a matching expression for the version of the policy set referenced
- **Version range**: specifies a range of version
- **Any version**
## Actions
| **Apply changes**
| Allows you to save the data of a new policy set reference or to update the data of a specific policy set reference. To save the data it will be mandatory to fill in the required fields
|
| **Undo**
| Allows you to quit without applying any changes.
|
| **Delete**
| Allows you to delete a policy set reference. You can choose that option on the hamburguer icon. To perform that action, Soffid will ask you for confirmation, you could confirm or cancel the operation.
|
| **Export**
| Allows you to export a XML file that contain the policy set reference.
|
| **Add new version**
| Allows you to add a new versión of the policy set reference
|
---
*http://docs.oasis-open.org/xacml/2.0/access\_control-xacml-2.0-core-spec-os.pdf*
# Target
## Description
Defines to which access requests a policy or rule applies. In XACML all the attributes are categorized into four main categories:
- [**Subjects**](#bkmrk-subjects)
- [**Resources**](#bkmrk-resources)
- [**Actions**](#bkmrk-actions)
- [ **Environments**](#bkmrk-environments)
A target can contains more than one subject, environment, resource or action or none of them. The target is the way to define the scope of an autorization policy. The result will be MATCHES if it all the target elements defined match.
- **Attribute Designator**: lets the policy specify an attribute with a given name and type, and optionally an issuer as well.
- **Attribute Value**: contains a literal attribute value.
## Screen
[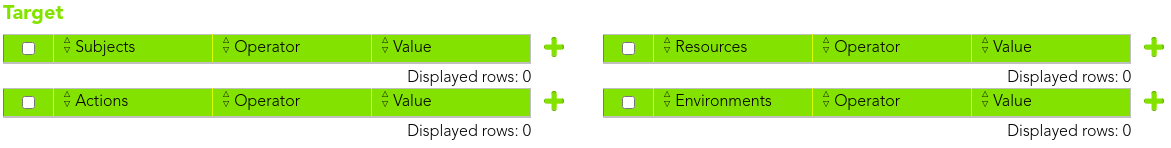](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628241373757.png)
## Related objects
- [**Policy set**](https://bookstack.soffid.com/books/xacml/page/policy-set "Policy set")
- [**Policy**](https://bookstack.soffid.com/books/xacml/page/policy "Policy")
- [**Rules**](https://bookstack.soffid.com/books/xacml/page/rules "Rules")
## Categories
### Subjects
> An actor whose attributes may be referenced by a predicate.
Represents the entity making a request for access to a resource.
Allows you to add one or more subjects as a target where the policy will be applied.
To configure a subject, first of all you need to select an attribute. You can select a value for an attribute designator list, or write the attribute selector value and select the data type.
Then, you need to select the operator, it will be used to compare or compute attributes.
And finally, you need to set a value, with which the attribute will be computed or compared. The value data type depends on the attribute data type.
### Resources
> Data, service or system component.
Allows you to add one or more resources as a target where the policy will be applied.
To configure a resource, first of all you need to select an attribute. You can select a value for a attribute designator list, or write the attribute selector value and select the data type.
Then, you need to select the operator, it will be used to compare or compute attributes.
And finally, you need to set a value, with which the attribute will be computed or compared. The value data type depends on the attribute data type.
### Actions
> An operation on a resource.
Allows you to add one or more actionss as a target where the policy will be applied.
To configure an action, first of all you need to select an attribute. You can select a value for a attribute designator list, or write the attribute selector value and select the data type.
Then, you need to select the operator, it will be used to compare or compute attributes.
And finally, you need to set a value, with which the attribute will be computed or compared. The value data type depends on the attribute data type.
### Environments
> The set of attributes that are relevant to an authorization decision and are independent of a particular subject, resource or action.
Allows you to add one or more environments as a target where the policy will be applied.
To configure an environment, first of all you need to select an attribute. You can select a value for a attribute designator list, or write the attribute selector value and select the data type. The
Then, you need to select the operator, it will be used to compare or compute attributes.
And finally, you need to set a value, with which the attribute will be computed or compared. The value data type depends on the attribute data type.
## Actions
The behavior of the actions is the same in each category, subjects, actions, resources and environments.
| **Add new**
| Allows you to add a new element to the list. To add a new element you need to click the add button, located at the end of the header and fulfill the form and save the data.
|
| **Delete**
| Allows you to delete an element to the variable list. To delete the element, you need to click the element you want to delete, and click the button with the subtraction symbol (-) at the end of the record.
To perform that action, Soffid will ask you for confirmation, you could confirm or cancel the operation.
|
| **Close**
| Allows you to save the data of a new element or to update the data of a specific element. To save the data it will be mandatory to fill in the required fields
|
| **Undo**
| Allows you to quit without applying any changes.
|
---
[*https://docs.oasis-open.org/xacml/2.0/access\_control-xacml-2.0-core-spec-os.pdf*](https://docs.oasis-open.org/xacml/2.0/access_control-xacml-2.0-core-spec-os.pdf)
# Rules
## Description
> A rule is the most elementary unit of policy. It may exist in isolation only within one of the major actors of the XACML domain. In order to exchange rules between major actors, they must be encapsulated in a policy. A rule can be evaluated on the basis of its contents.
Each rule sets a specific condition for allowing or denying access to a resource.
A rule is composed by a target, an effect and a condition. It is able to add more than one rule to the policy.
## Screen overview
[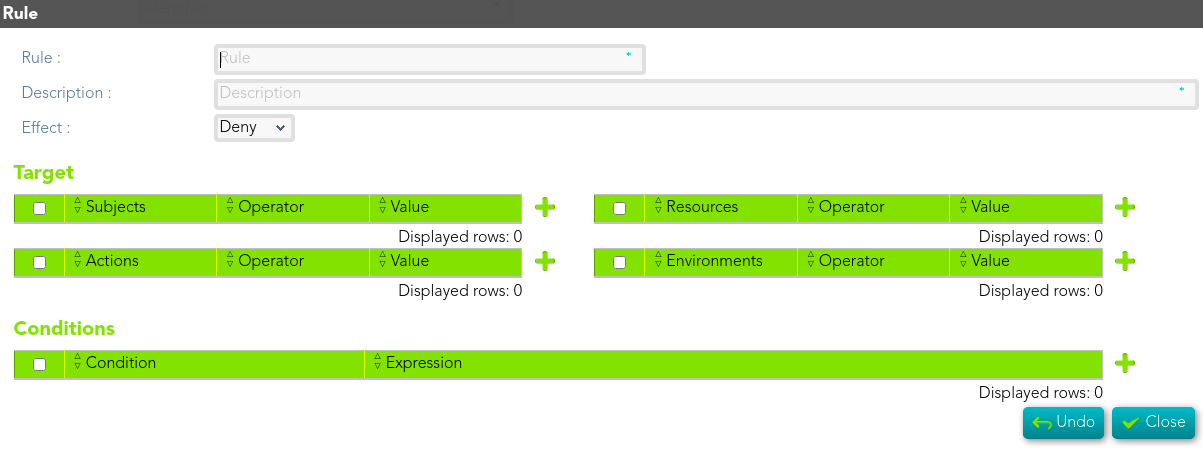](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628241401441.png)
## Related objects
- [**Policy**](https://bookstack.soffid.com/books/xacml/page/policy "Policy")
- [**Target**](https://bookstack.soffid.com/books/soffid-3-reference-guide/page/agents "Agents")
- [**Conditions**](https://bookstack.soffid.com/books/xacml/page/conditions "Conditions")
## Standard attributes
- **Rule**: rule name.
- **Description**: brief description of the rule.
- **Effect**: "Rule effect declaration. When a rule evaluates to ‘True’ it emits the value of the Effect attribute. This value is then combined with the Effect values of other rules according to the rule combining algorithm."Two values are allowed:
- Permit.
- Deny.
- [**Target**](https://bookstack.soffid.com/books/soffid-3-reference-guide/page/agents "Agents")
- [**Conditions**](https://bookstack.soffid.com/books/xacml/page/conditions "Conditions")
## Actions
| **Add new**
| Allows you to add a new rule to the rules list. To add a new rule you need to click the add button, located at the end of the header and fulfill the form and save the data.
|
| **Delete**
| Allows you to delete a rule to the rules list. To delete the rule, you need to click the rule you want to delete, and click the button with the subtraction symbol (-) at the end of the record.
To perform that action, Soffid will ask you for confirmation, you could confirm or cancel the operation.
|
| **Close**
| Allows you to save the data of a new rule or to update the data of a specific variable. To save the data it will be mandatory to fill in the required fields
|
| **Undo**
| Allows you to quit without applying any changes.
|
---
[*https://docs.oasis-open.org/xacml/2.0/access\_control-xacml-2.0-core-spec-os.pdf*](https://docs.oasis-open.org/xacml/2.0/access_control-xacml-2.0-core-spec-os.pdf)
# Variables
## Description
> Variables are the elements to define functions that may be used througthout the policy.
## Screen overview
[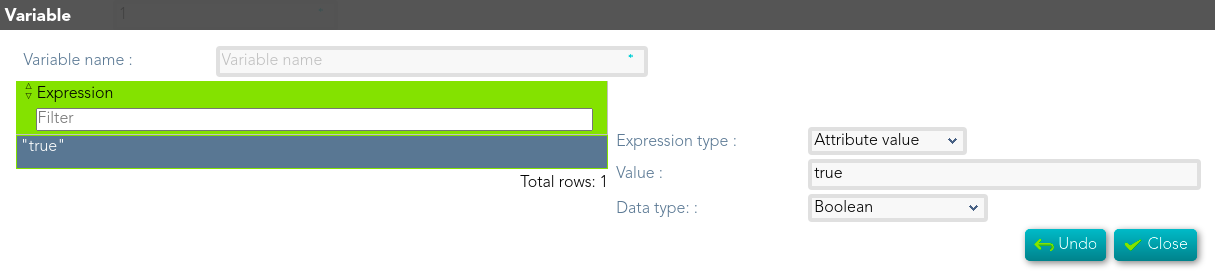](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628241435635.png)
## Related objects
- [**Policy**](https://bookstack.soffid.com/books/xacml/page/policy "Policy")
- [**Expressions**](https://bookstack.soffid.com/books/xacml/page/expressions "Expressions")
## Standard attributes
- **Variable name**: Name to identify the variable.
- [**Expressions**](https://bookstack.soffid.com/books/xacml/page/expressions "Expressions"): Any element of ExpressionType complex type.
## Actions
| **Add new**
| Allows you to add a new variable to the variables list. To add a new variable you need to click the add button, located at the end of the header and fulfill the form and save the data.
|
| **Delete**
| Allows you to delete a variable to the variable list. To delete the variable, you need to click the variable you want to delete, and click the button with the subtraction symbol (-) at the end of the record.
To perform that action, Soffid will ask you for confirmation, you could confirm or cancel the operation.
|
| **Close**
| Allows you to save the data of a new variable or to update the data of a specific variable. To save the data it will be mandatory to fill in the required fields
|
| **Undo**
| Allows you to quit without applying any changes.
|
---
[*https://docs.oasis-open.org/xacml/2.0/access\_control-xacml-2.0-core-spec-os.pdf*](https://docs.oasis-open.org/xacml/2.0/access_control-xacml-2.0-core-spec-os.pdf)
# Obligations
## Description
> XACML defines obligations as actions that have to be returned to the PEP with the PDP response XACML .
>
> If the PDP's evaluation is viewed as a tree of rules, policy sets and policies, each of which returns "Permit" or "Deny", then the set of obligations returned by the PDP to the PEP will include only the obligations associated with those paths where the effect at each level of evaluation is the same as the effect being returned by the PDP.
## Screen Overview
[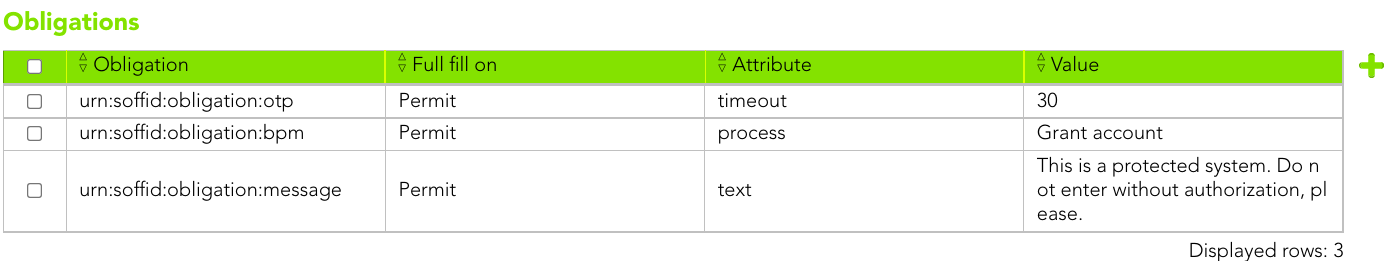](https://bookstack.soffid.com/uploads/images/gallery/2022-02/image-1643698881614.png)
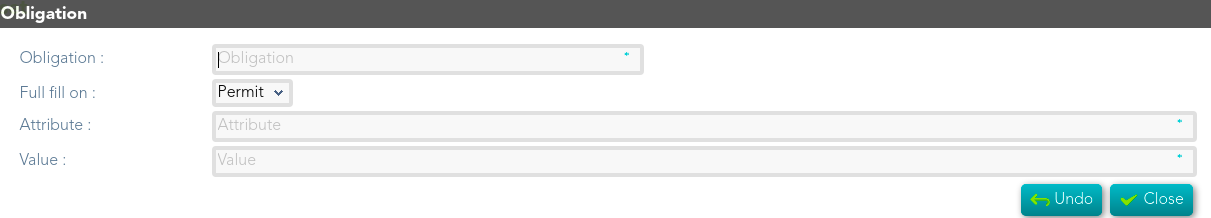
#### Add Obligation
[](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628241474697.png)
## Related objects
- [**Policy set**](https://bookstack.soffid.com/books/xacml/page/policy-set "Policy set")
- [**Policy**](https://bookstack.soffid.com/books/xacml/page/policy "Policy")
## Standard attributes
- **Obligation**:
- urn:soffid:obligation:otp
- urn:soffid:obligation:message
- urn:soffid:obligation:bpm
- urn:soffid:obligation:session-recording
- urn:soffid:obligation:notify-owner
- **Full fill on**:
- Permit
- Deny
- **Attribute**:
- **text**: message that will be showed.
- **process**: process that will be launched.
- **timeout**: period of time the otp code will be valid for.
- **Value**: the value of the attribute.
| **OBLIGATION** | **ATTRIBUTE** |
| urn:soffid:obligation:otp | timeout |
| urn:soffid:obligation:message | text |
| urn:soffid:obligation:bpm | process |
## Actions
| **Add new**
| Allows you to add a new obligation to the obligations list. To add a new obligation you need to click the add button, located at the end of the header and fulfill the form and save the data.
|
| **Delete**
| Allows you to delete an obligation to the obligations list. To delete the obligation, you need to click the obligation you want to delete and click the button with the subtraction symbol (-) at the end of the record.
To perform that action, Soffid will ask you for confirmation, you could confirm or cancel the operation.
|
| **Close**
| Allows you to save the data of a new variable or to update the data of a specific variable. To save the data it will be mandatory to fill in the required fields
|
| **Undo**
| Allows you to quit without applying any changes.
|
---
*http://www.oasis-open.org/committees/xacml/*
# Conditions
## Description
> Condition represents a Boolean expression that refines the applicability of the rule beyond the predicates implied by its target. Therefore, it may be absent.
## Screen overview
[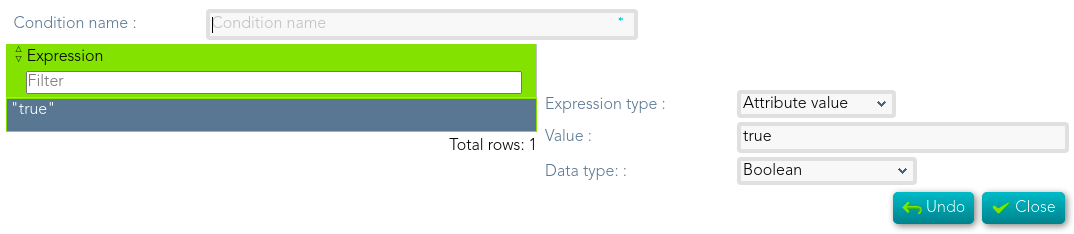](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628241514842.png)
## Related objects
- [**Policy**](https://bookstack.soffid.com/books/xacml/page/policy "Policy")
- [**Expressions**](https://bookstack.soffid.com/books/xacml/page/expressions "Expressions")
## Standard attributes
- **Condition name**: Name to identify the condition.
- [**Expressions**](https://bookstack.soffid.com/books/xacml/page/expressions "Expressions"): any element of ExpressionType complex type that return true or false.
## Actions
| **Add new**
| Allows you to add a new condition to the conditions list. To add a new condition you need to click the add button, located at the end of the header and fulfill the form and save the data.
|
| **Delete**
| Allows you to delete a condition to the variable list. To delete the condition, you need to click the condition you want to delete, and click the button with the subtraction symbol (-) at the end of the record.
To perform that action, Soffid will ask you for confirmation, you could confirm or cancel the operation.
|
| **Close**
| Allows you to save the data of a new condition or to update the data of a specific condition. To save the data it will be mandatory to fill in the required fields
|
| **Undo**
| Allows you to quit without applying any changes.
|
---
[*https://docs.oasis-open.org/xacml/2.0/access\_control-xacml-2.0-core-spec-os.pdf*](https://docs.oasis-open.org/xacml/2.0/access_control-xacml-2.0-core-spec-os.pdf)
# Expressions
## Description
> The Expression signifies that an element that extends the ExpressionType and is a member of the Expression substitution group shall appear in its place. The Expression is not used directly in a policy.
Expressions are elements that allow to evaluate conditions within rules and policies to make access decisions.
## Related objects
- [**Variables**](https://bookstack.soffid.com/books/xacml/page/variables "Variables")
- [**Conditions**](https://bookstack.soffid.com/books/xacml/page/conditions "Conditions")
## Standard attributes
The attributes depend on the Expression type selected.
## Data Type
Available data types
- String:
- Boolean
- Integer
- Double
- Date and time
- Date
- Time
- HEX-encoded binary
- URI
- Year-month duration
- Day-time duration
- Base 64 binary
- X. 500 name
- RFC822 name
---
[*https://docs.oasis-open.org/xacml/2.0/access\_control-xacml-2.0-core-spec-os.pdf*](https://docs.oasis-open.org/xacml/2.0/access_control-xacml-2.0-core-spec-os.pdf)
# XACML Examples
XACML Examples
# Example Web PEP
## Web Policy Enforcement Point
### Use case example
We want to define a policy to restrict access to some pages of the Soffid console.
The users who are assigned to the SOFFID\_RRHH role (from this point forward: end-users) will have limitations to access to some Soffid console pages:
1. The end-users who belong to the "enterprise" group as primary group, could not access to the groups page.
2. The end-users could not access to role page.
3. En other cases permit access.
### XACML Editor
#### Policy set
First of all, we define a policy set.
[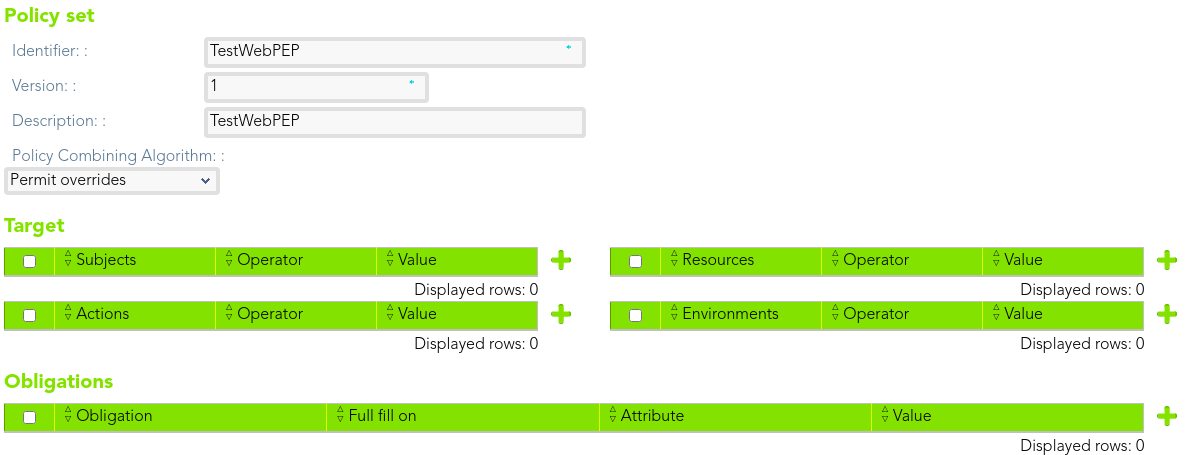](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628237637437.png)
#### Policy
Then, we can define a policy to manage the access. We need to define the subject, in that case users with SOFFID\_RRHH role assigned.
Also, we can define a variable that contains the group name to establish the restrictions.
[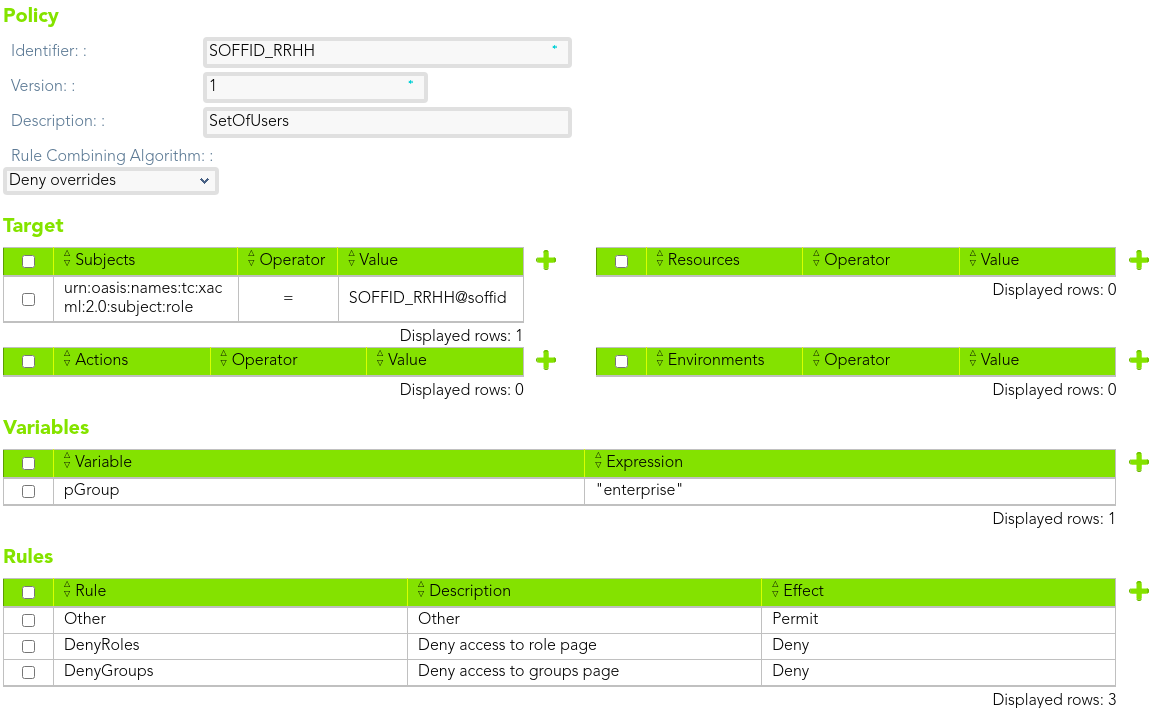](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628237773318.png)
#### Rule 1
> The end-users who belong to the "enterprise" group as primary group, could not access to the groups page.
[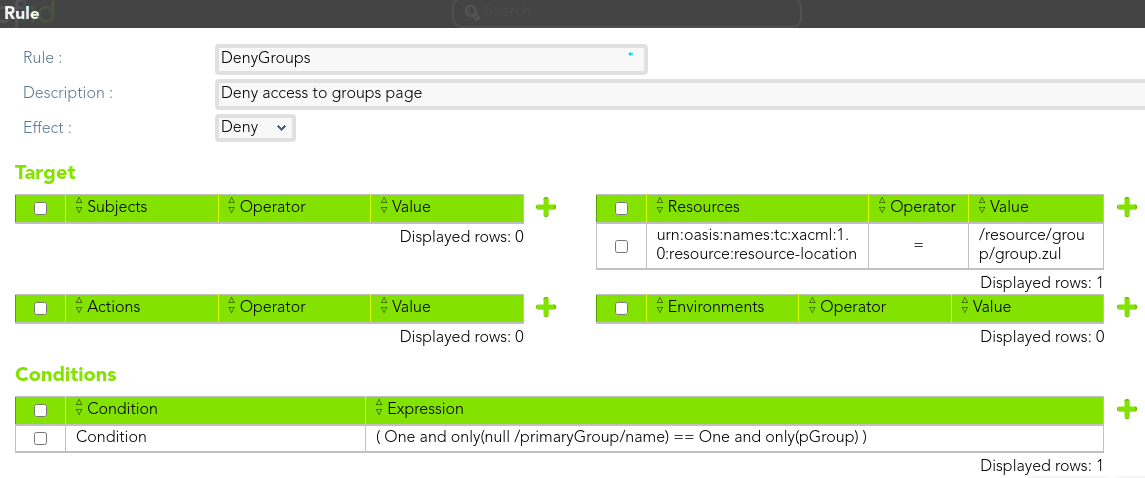](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628238106719.png)
#### Rule 2
> The end-users could not access to role page.
[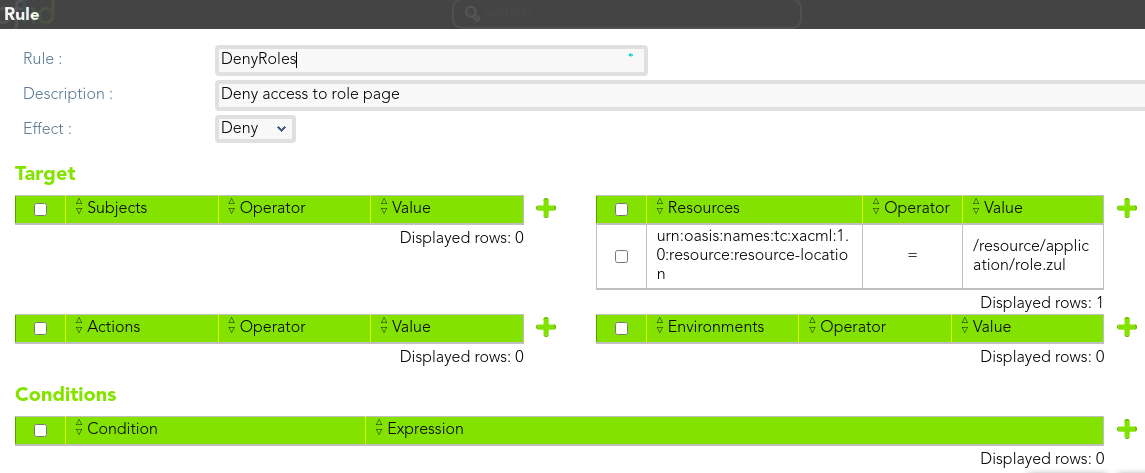](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628238134714.png)
#### Rule 3
> En other cases permit access.
[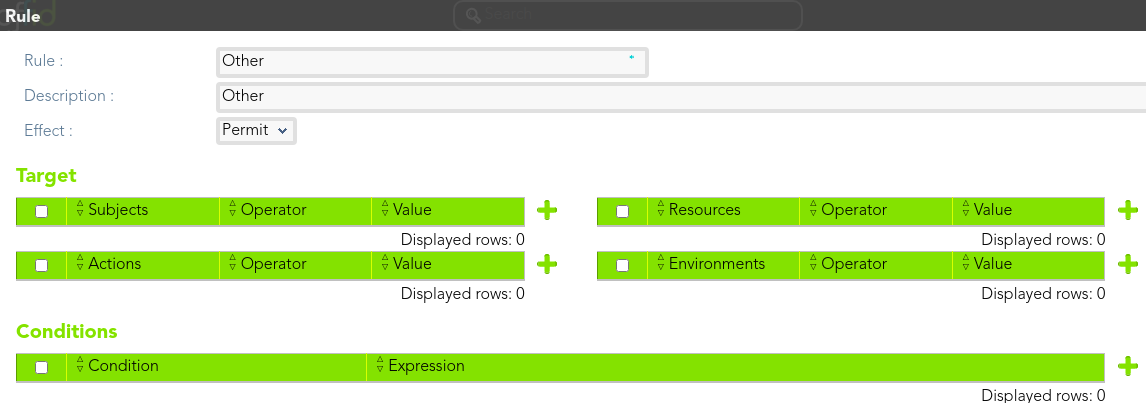](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628238162313.png)
### Download XML
You can download a XML file with the example: [policy-TestWebPEP.xml](https://bookstack.soffid.com/attachments/22)
## Configure PEP
[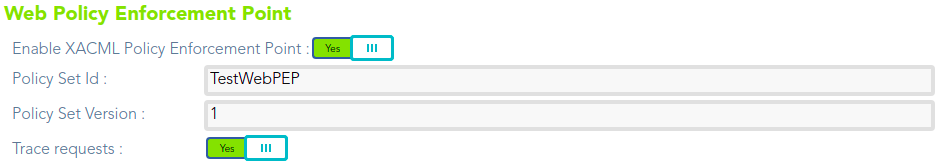](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628235091281.png)
# Example Role centric PEP
## Role centric Enforcement Point
### Use case example
We want to define a policy to restrict access to the Soffid console role's page (MainMenu > Administration > Resources > Roles).
The users who belong to the "enterprise" group as primary group (from this point forward: *end-users*) will have limitations to perform some actions on the Soffid console roles page.
1. The *end-users* could query all the roles information.
2. The *end-users* could update any role in the information systems "ERP RRHH"
3. The *end-users* could not create any role.
4. The *end-users* could not delete any role.
### XACML Editor
#### Policy set
First of all, we define a policy set. We need to define the subject, in that case users who belong to "enterprise" as primary group.
[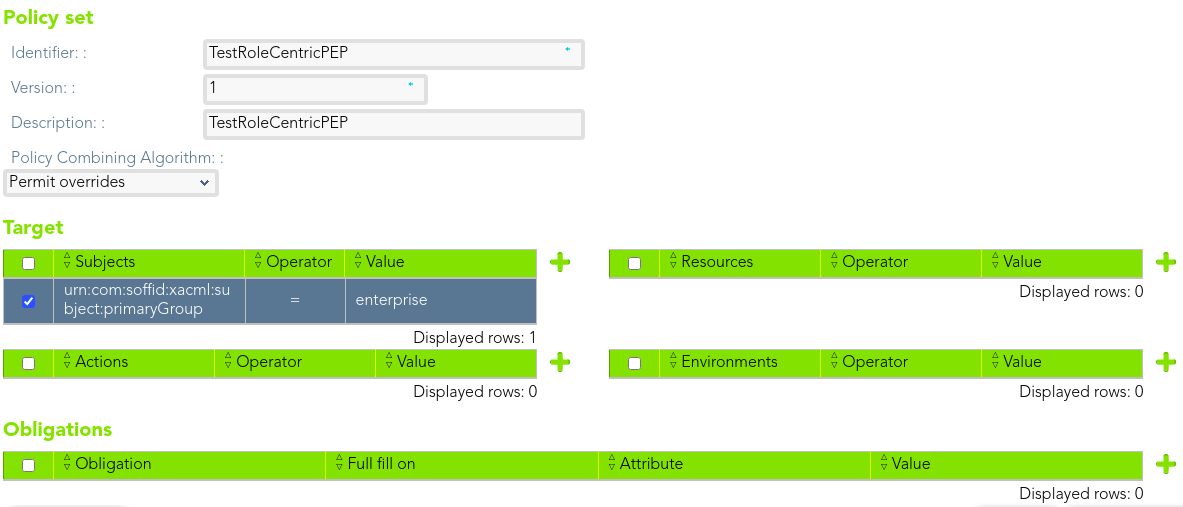](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628238451051.png)
Then, we can define a policy to manage the different actions that the *end-users* could perform.
[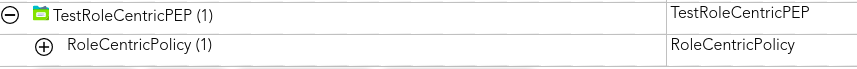](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628238488177.png)
#### Policy
The policy will apply to an only one user. That policy will be to protect the role resource.
[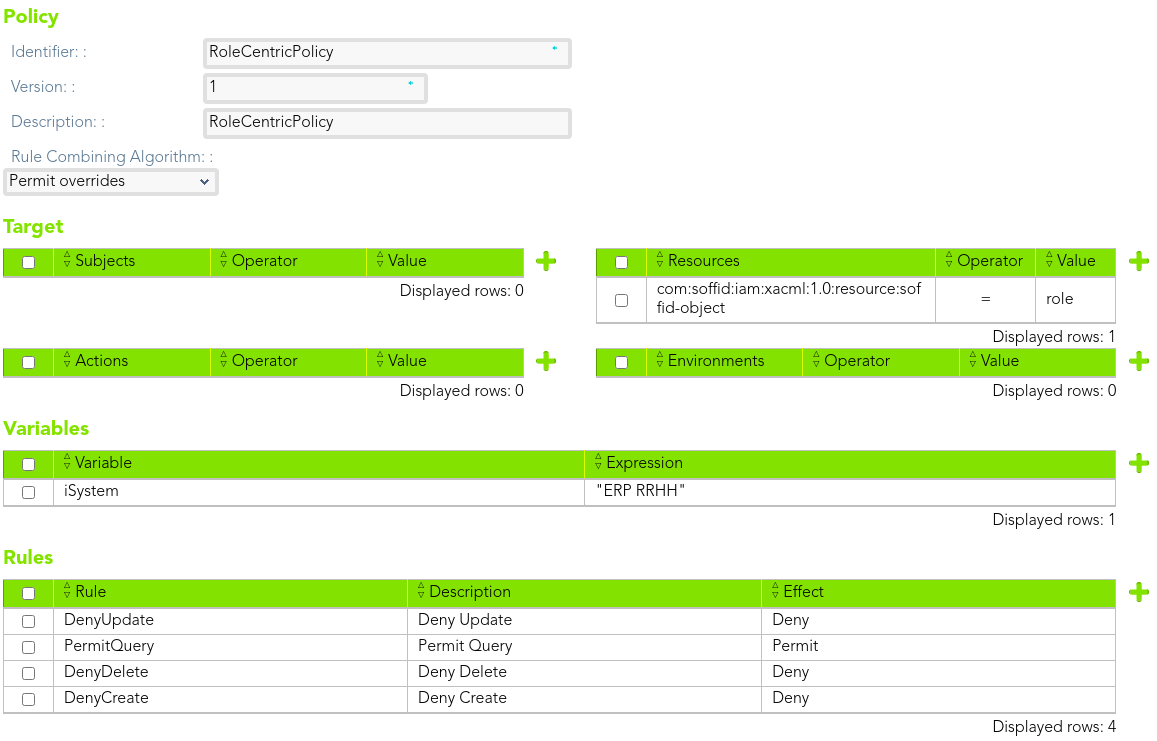](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628238516436.png)
##### Rule 1
> The *end-users* could query all the roles information.
We define the rule that allow to the end-users to query all the roles information.
[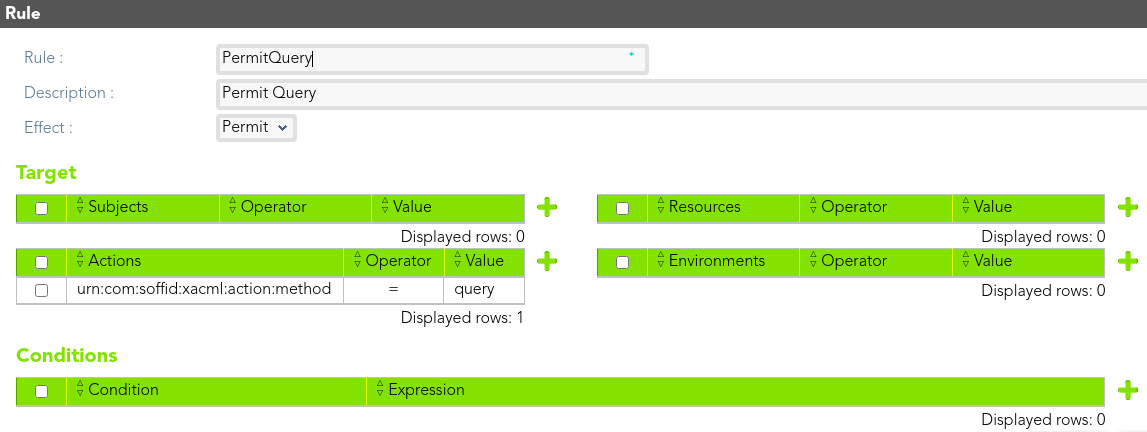](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628238550714.png)
##### Rule 2
> The *end-users* could update any role in the information systems "ERP RRHH"
[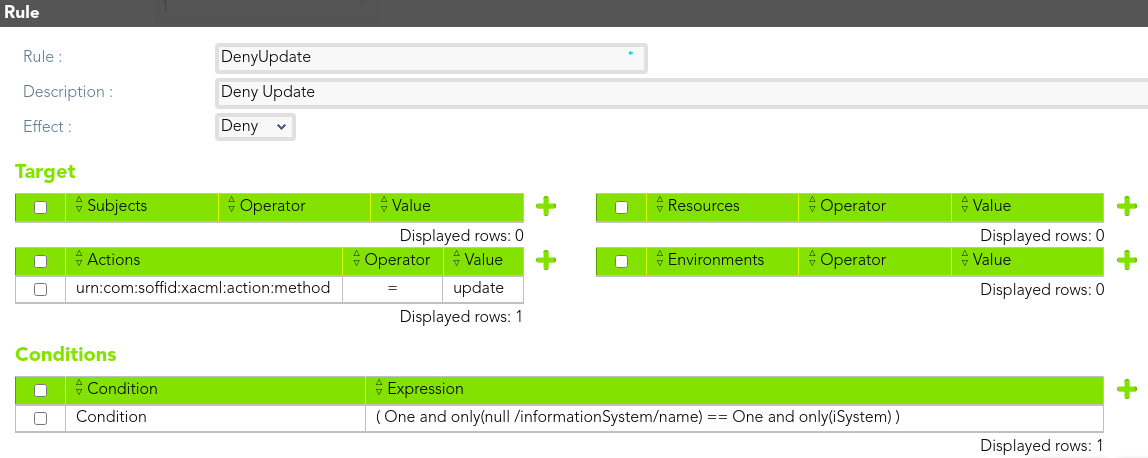](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628238577406.png)
##### Rule 3
> The *end-users* could not create any role.
[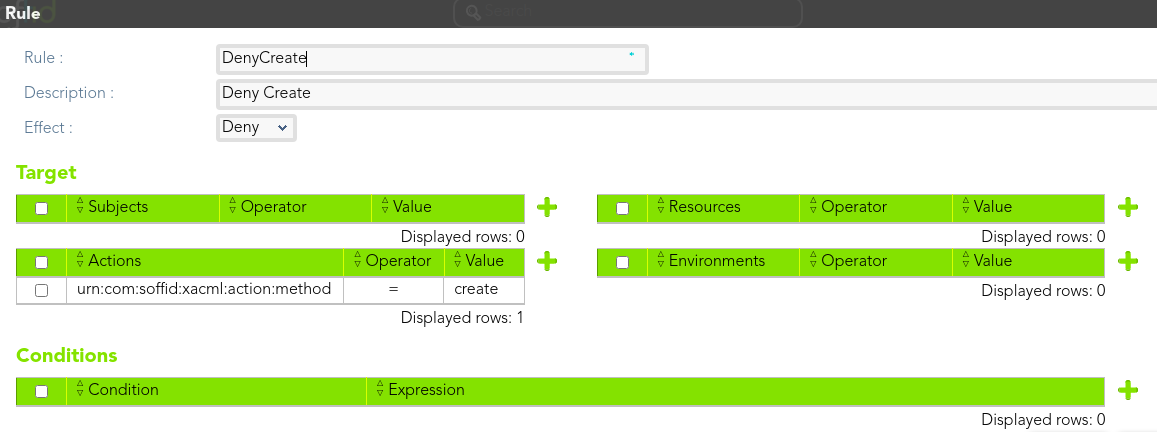](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628238610498.png)
##### Rule 4
> The *end-users* could not delete any role.
[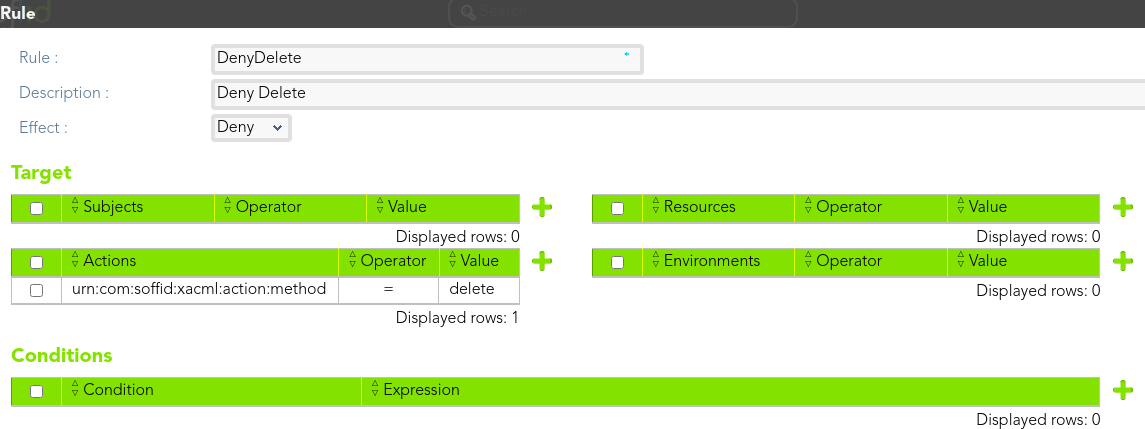](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628238769335.png)
### Download XML
You can download a XML file with the example: [policy-TestRoleCentricPEP.xml](https://bookstack.soffid.com/attachments/21)
## Configure PEP
[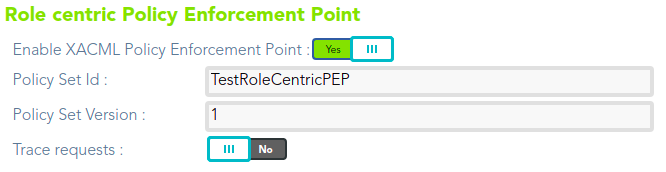](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628238733004.png)
# Example Dynamic role PEP
## Dynamic role Enforcement Point
### Use case example
We want to define a policy to restrict access to the Soffid console user's page (MainMenu > Administration > Resources > Users).
The users who are assigned to the SOFFID\_RRHH role (from this point forward: *end-users*) will have limitations to perform some actions on the Soffid console users page:
1. The *end-users* only be able to query the information about the users who belong to the same primary group that them.
2. The *end-users* only be able to update the users with internal user type.
3. The *end-users* could not delete any user record.
### XACML Editor
#### Policy set
First of all, we define a policy set. We need to define the subject, in that case users with SOFFID\_RRHH role assigned.
[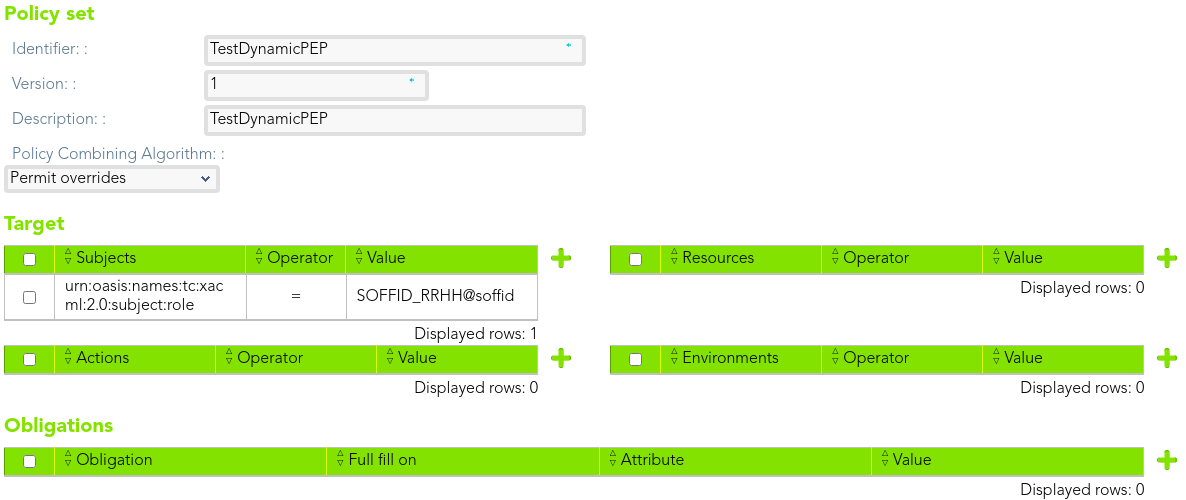](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628231702828.png)
Then, we can create the policies, in that case, we can create three policies, one for each operation that we want to manage.
[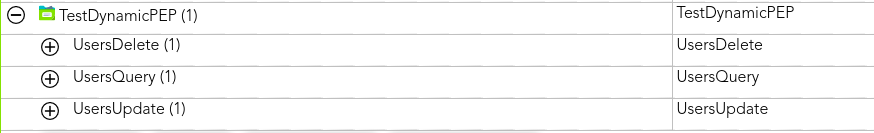](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628238915331.png)
#### Policies
We can define a policy for each operation, to permit or deny access.
Also, we can define a variable that contains the *end-user* primary group in order to use it when we define the conditions.
##### Policy1
> The *end-users* only be able to query the information about the users who belong to the same primary group that them.
We need to define two rules, one to permit and other to deny access.
[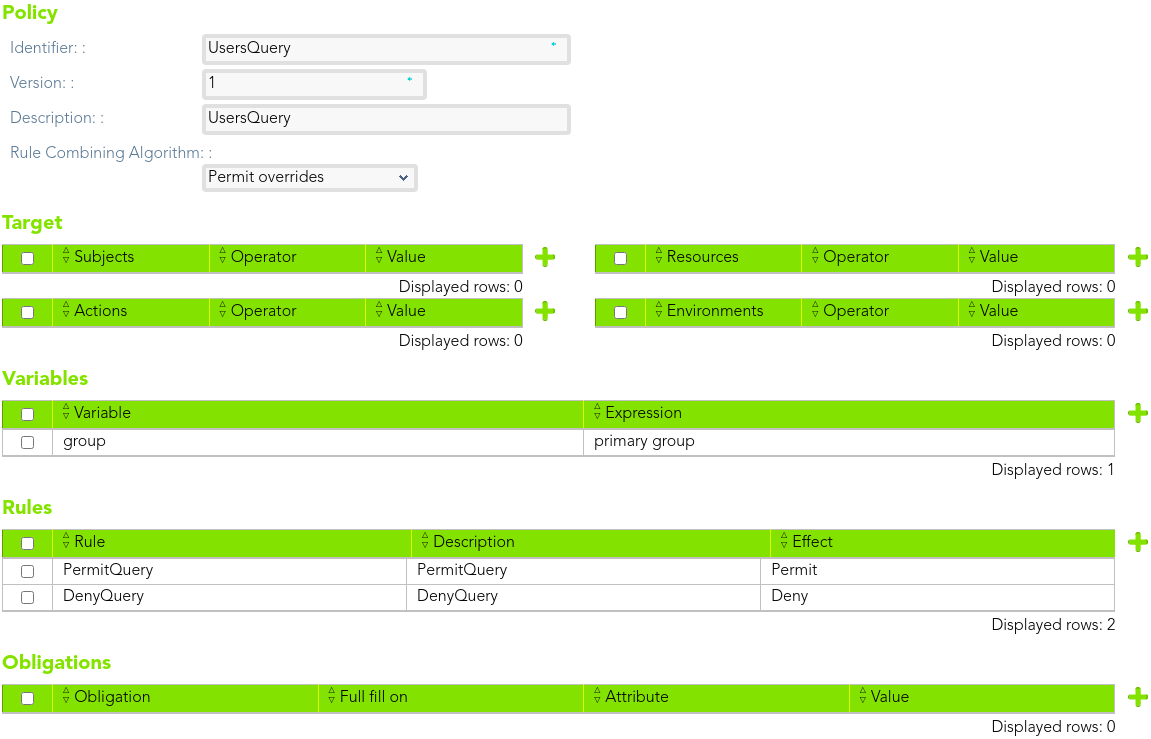](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628238946431.png)
##### Rules
We define the rule that allow to the *end-user* to query users information who belong to the same primary group that the end-user.
[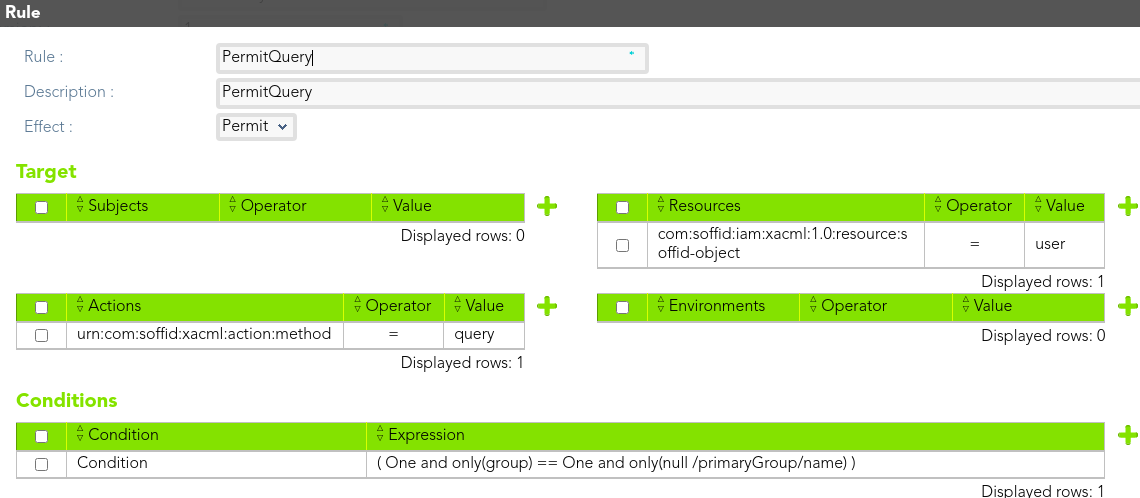](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628238975450.png)
Then, we define the rule that denies access to *end-users* to query users information.
[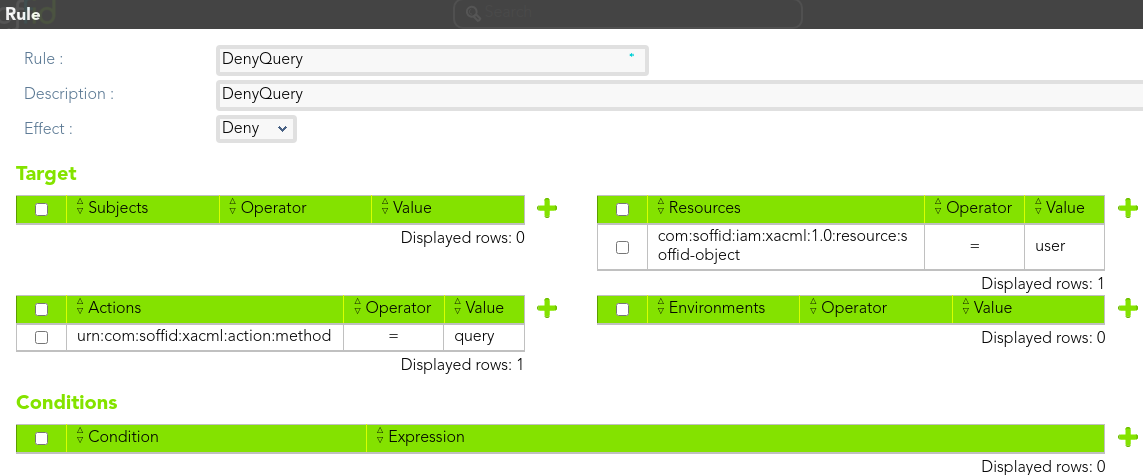](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628239000393.png)
##### Policy 2
> The *end-users* only be able to update the users with internal user type.
We need to define two rules, one to permit and other to deny access.
[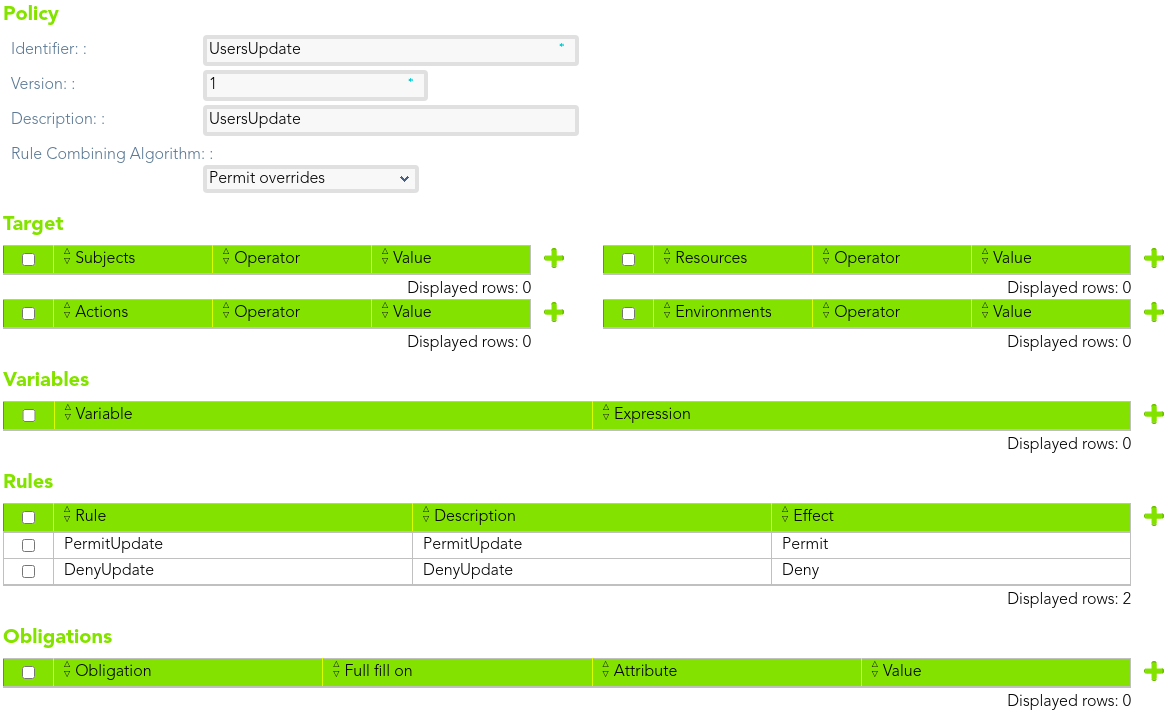](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628239036221.png)
##### Rules
We define the rule that allow to the *end-users to* update users information who are internal users.
[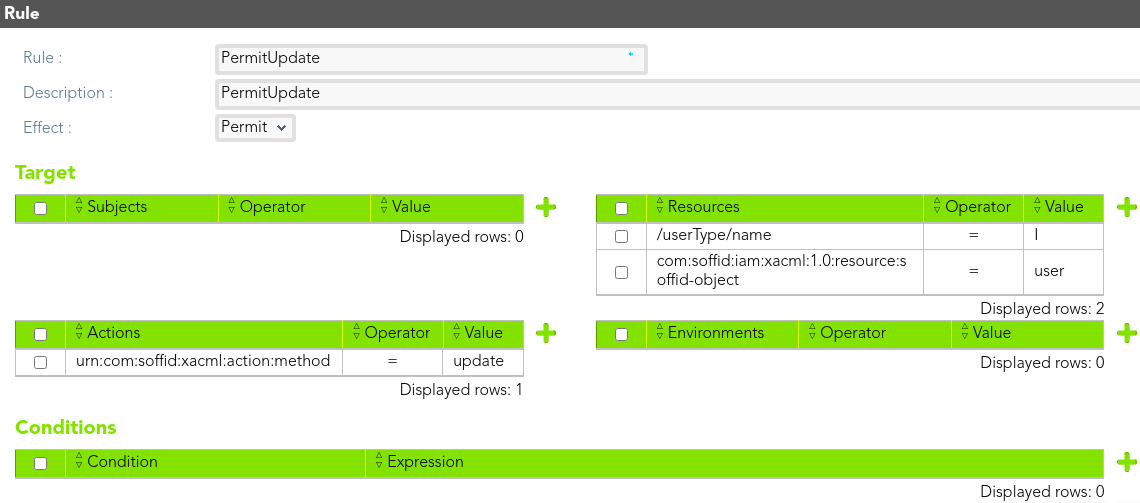](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628239076738.png)
Then, we define the rule that denies access to *end-users* to update users information.
[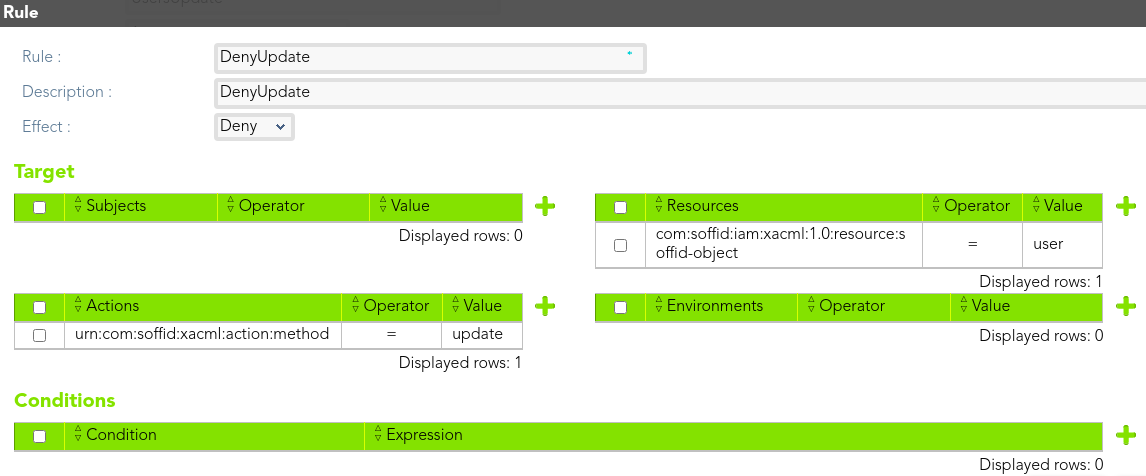](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628239102464.png)
##### Policy 3
> The *end-users* could not delete any user record.
We need to define only one rule to deny access.
[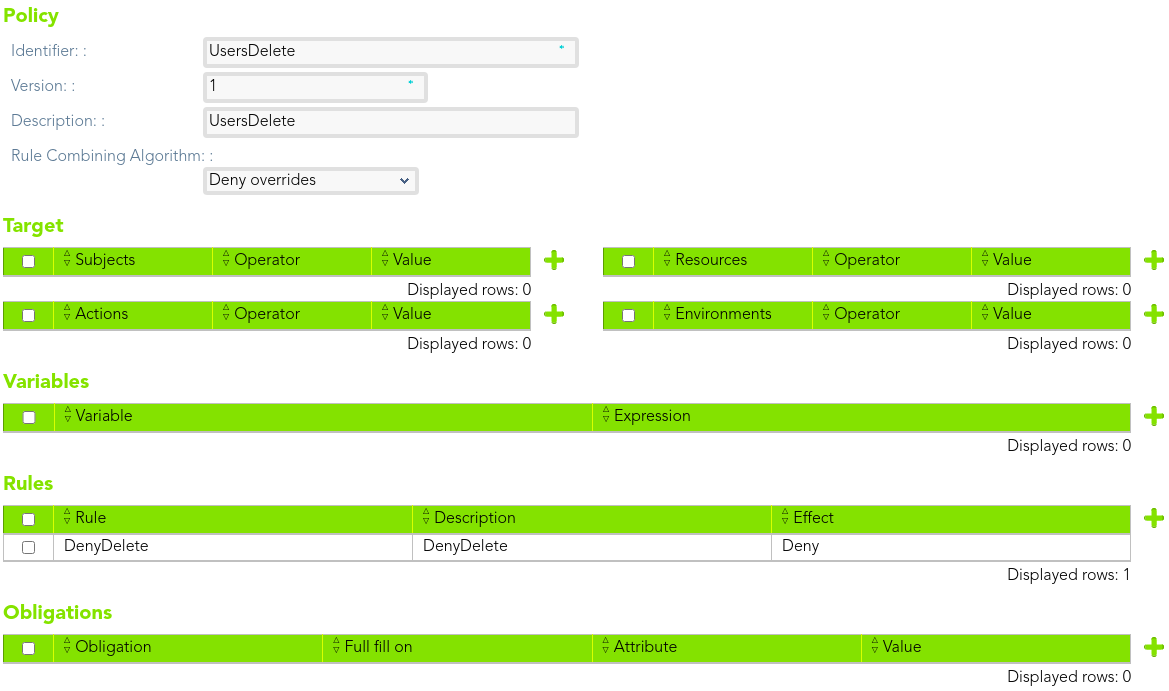](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628239130798.png)
##### Rules
We define the rule that deny to the *end-user* delete any user.
[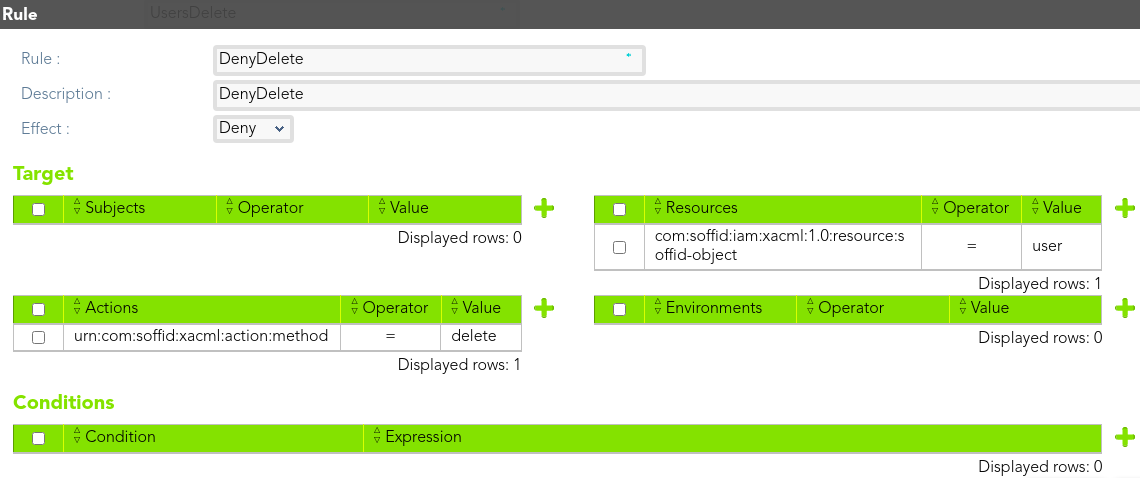](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628239173903.png)
### Download XML
You can download a XML file with the example: [policy-TestDynamicPEP.xml](https://bookstack.soffid.com/attachments/20)
## Configure PEP
[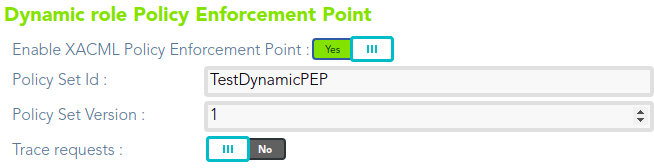](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628238841651.png)
# Example Password Vault PEP
## Password Vault Policy Enforcement Point
### Use case example 1
We want to define a policy to restrict access to the Soffid Password Vault.
The users who are assigned to the SOFFID\_ADMIN role (from this point forward: end-users) will have limitations to perform some actions on the folder "demoFolder" of the Soffid Password Vault
1. The end-users only be able to access the accounts of that folder on labor time. The permissions will be denied in another case.
### Policy set
First of all, we define a policy set that could contain other policy sets and policies.
[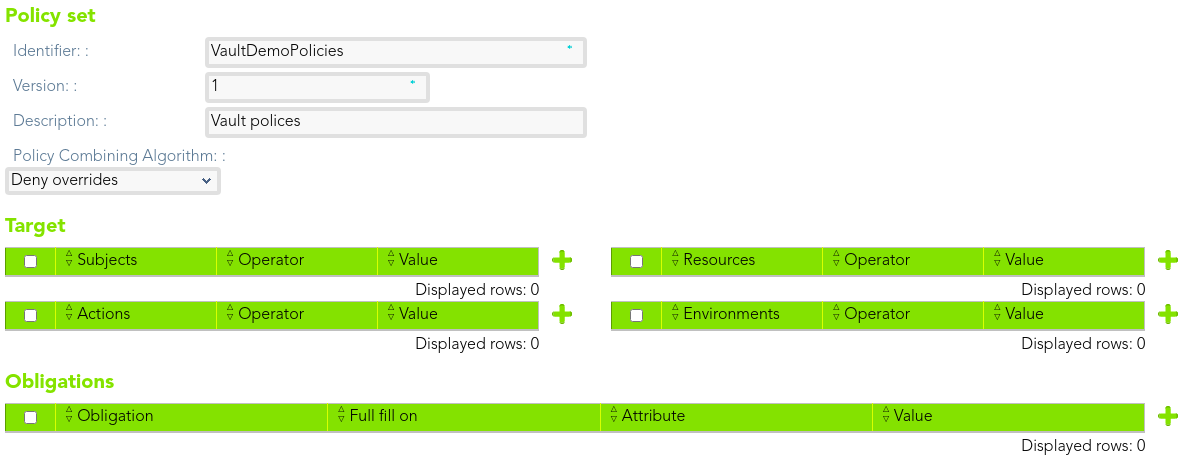](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628240486192.png)
### Policy set 2
Then, we can create another policy set as a child of the former to manage the folder and to define the subject, in that case, users with SOFFID\_ADMIN role assigned.
[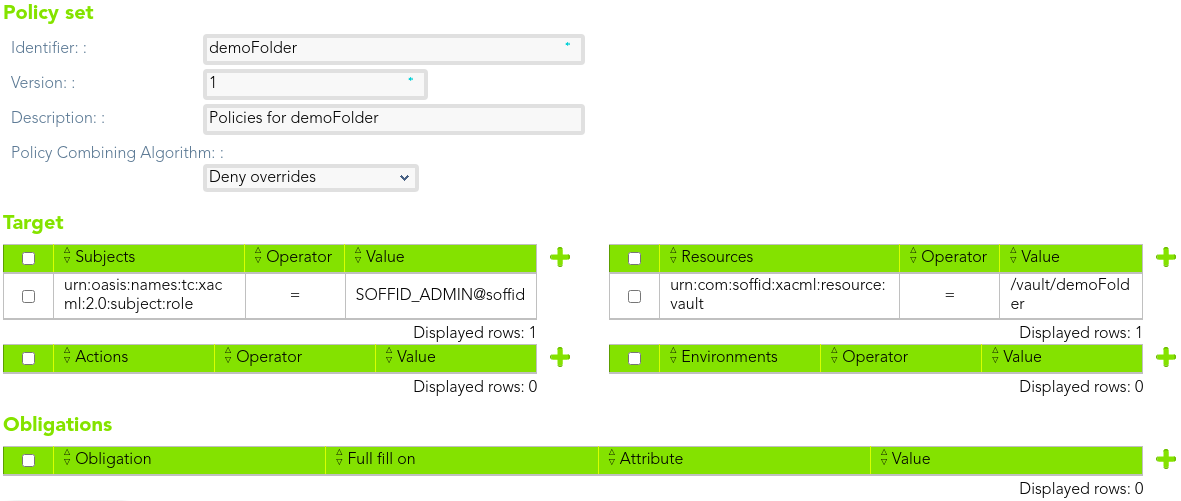](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628240781296.png)
That policy set will contain the policies.
[](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628240820879.png)
### Policies
#### Policy 1
> The end-users only be able to access the accounts of that folder on labour time. The permissions will be denied in other case.
[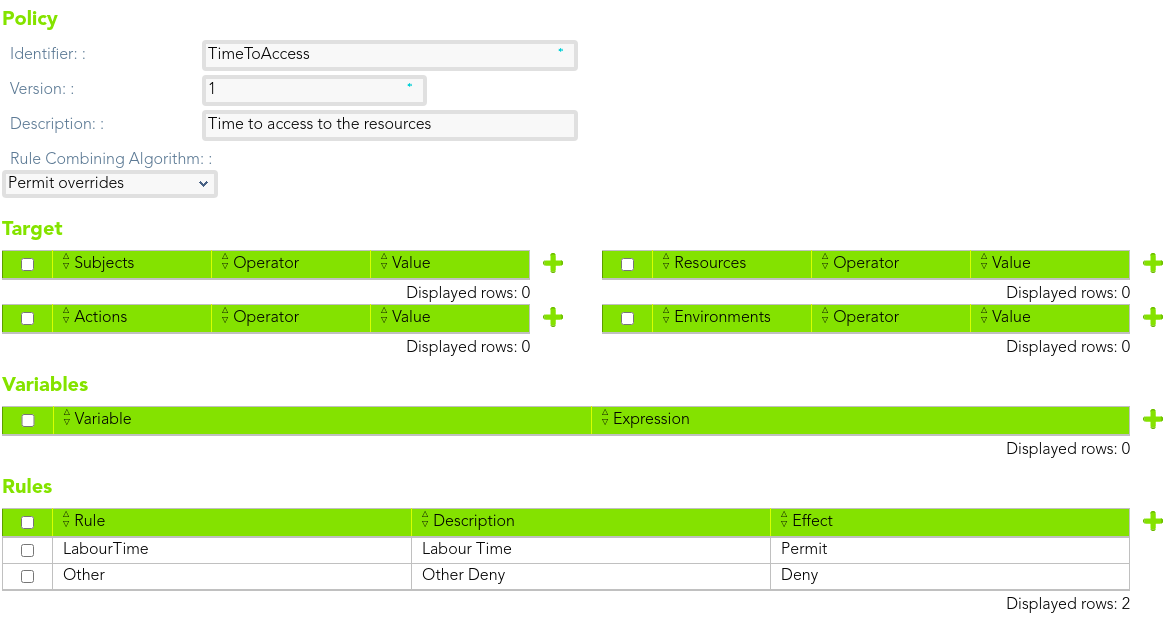](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628240889871.png)
##### Rule
We define the rule that permit access to the *end-user*
[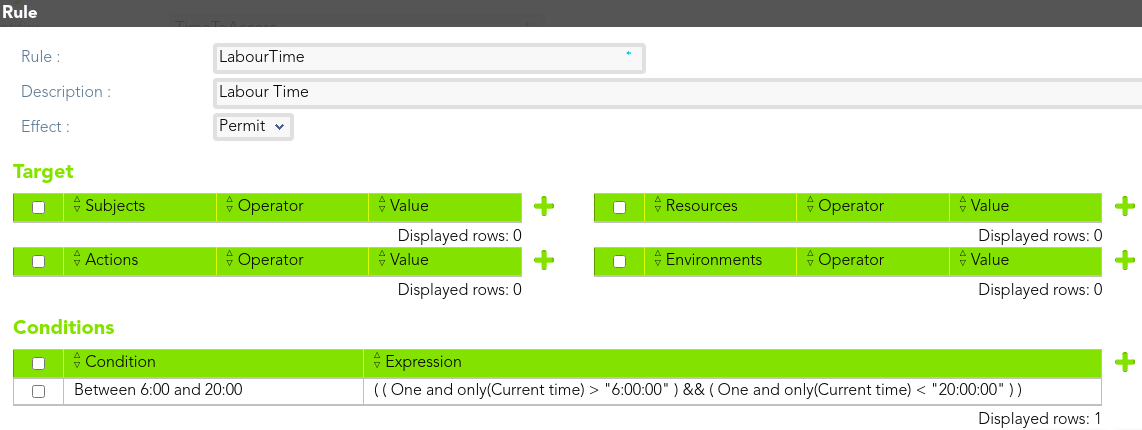](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628241172154.png)
And we define other to deny access.
[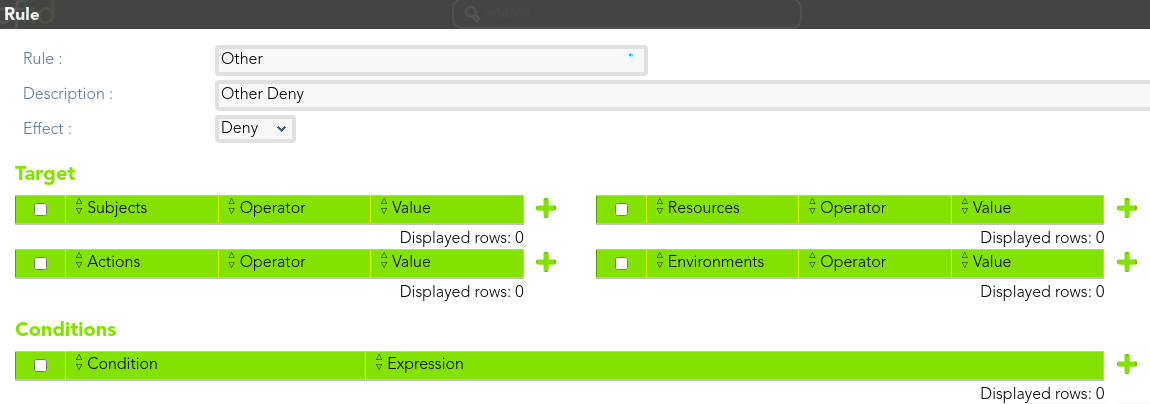](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628241209362.png)
### Use case example 2
We want to define a policy to restrict access to the Soffid Password Vault.
The users who are assigned to the SOFFID\_ADMIN role (from this point forward: end-users) will have limitations to perform some actions on the folder "demoFolder" of the Soffid Password Vault
1. The end-users only be able to access the accounts of that folder on labor time. The permissions will be denied in another case. (Use case example 1)
2. To connect there are some obligations to fulfill
[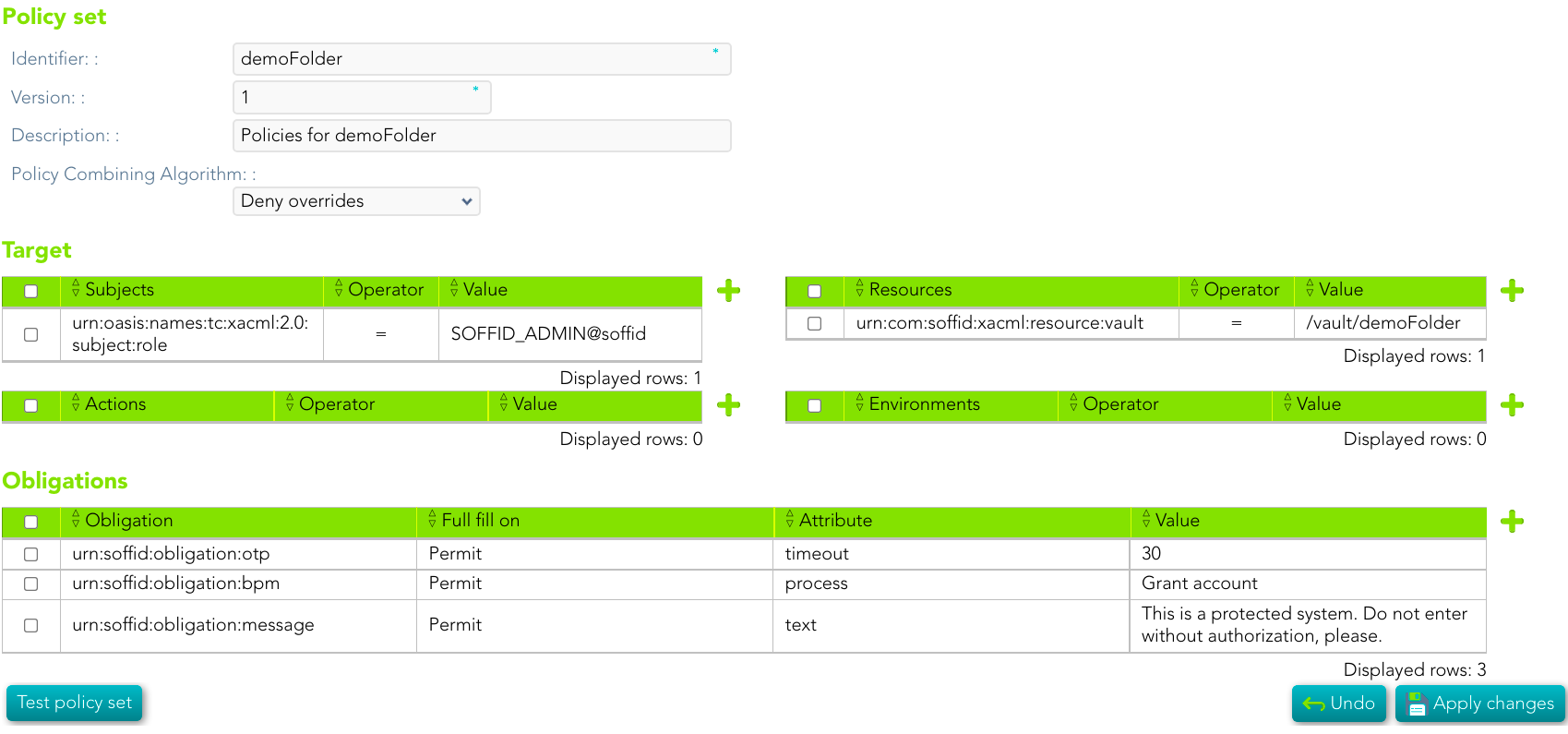](https://bookstack.soffid.com/uploads/images/gallery/2022-02/image-1643698970894.png)
### Use case example 3
We want to define a policy to restrict access to the Soffid Password Vault.
The access will be denied on Sunday.
[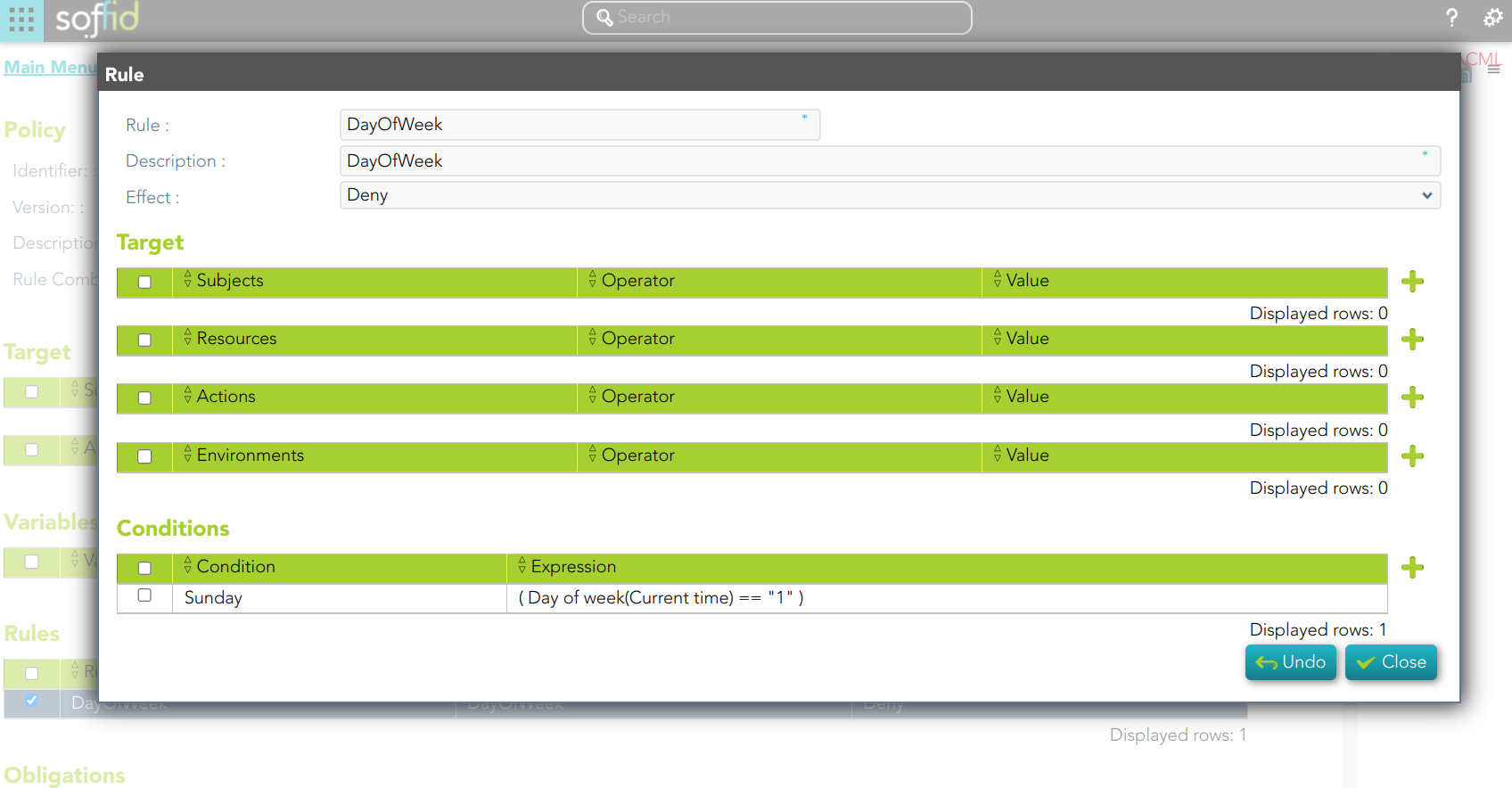](https://bookstack.soffid.com/uploads/images/gallery/2023-09/image-1695648483304.png)
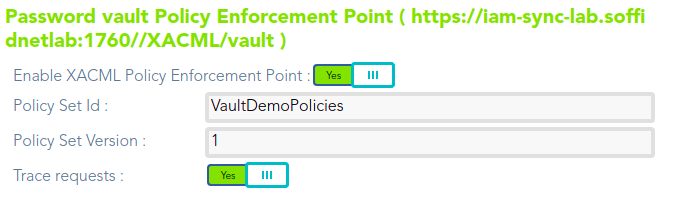
### Download XML
You can download an XML file with the example: [policy-demoFolder.xml](https://bookstack.soffid.com/attachments/23)
## Configure PEP
[](https://bookstack.soffid.com/uploads/images/gallery/2021-08/image-1628239716307.png)