Soffid console provides a granular access control system. That granular control system allows the administrator user to assign granular permissions to roles. Be in mind that some permissions may inherit some other permissions.
You cannot assign permissions directly to users. Instead, permissions are assigned to roles and roles are assign to users, either directly or through grant inheritance. The roles may be created into Soffid application system, but could also be included in any other application system. Permissions are grouped into permission scopes. Most scopes are Soffid object types, but there are one special scope named Soffid, that applies to Soffid console web pages. Addons can create their own authorizations that automatically will appear at this screen. When a new addon has been installed and applied, the first thing to do use to be assign permissions for this new addon. In fact, administrators won't be able to manage the addon unless the log out and log in to get the newly created permissions. The permissions given to roles and the roles given to users are cached by Soffid. In order to reapply permissions, the user should close its session and log-in again ## Screen overview [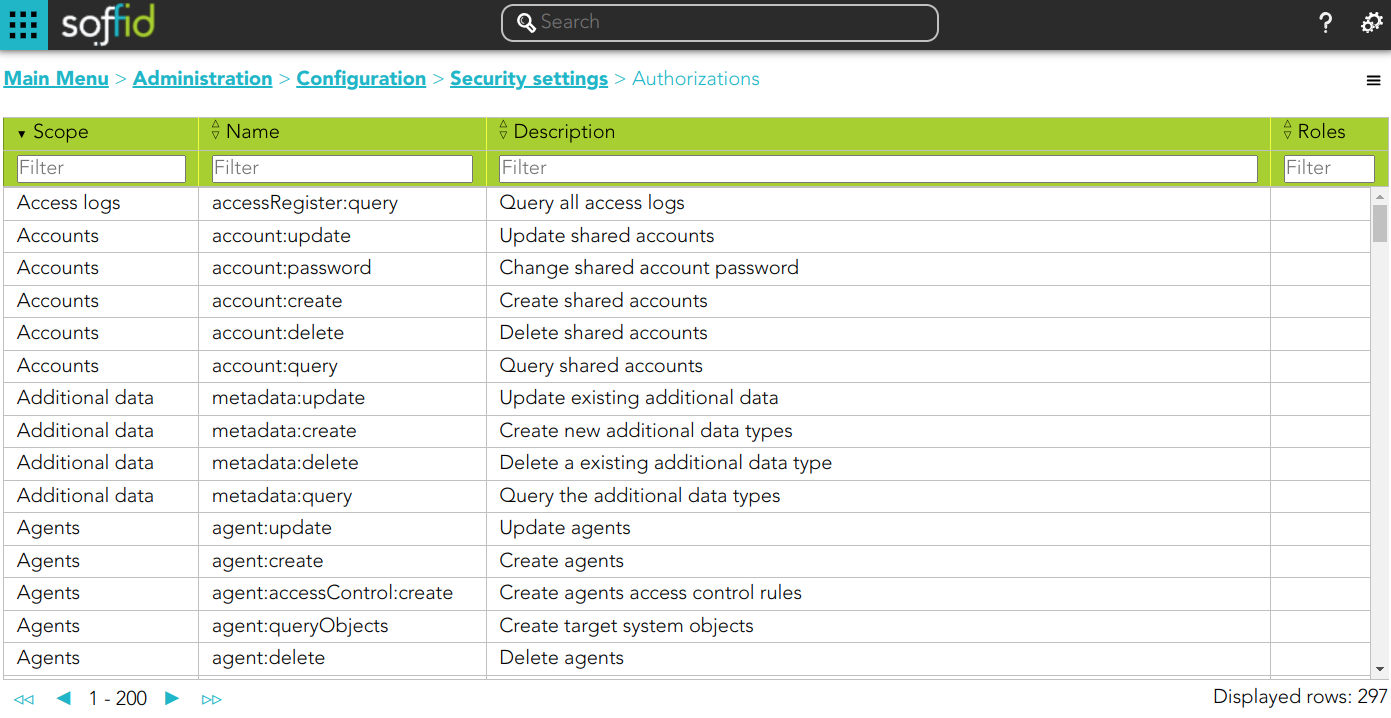](https://bookstack.soffid.com/uploads/images/gallery/2024-03/image-1711094581997.png) ## Related objects 1. [**Roles**](https://bookstack.soffid.com/books/soffid-3-reference-guide/page/roles "Roles") 2. [**Information system**](https://bookstack.soffid.com/books/soffid-3-reference-guide/page/information-systems "Information systems") ## Standard attributes - **Scope**: scope of application. - **Name**: name of the granular permission. - **Description**: brief description of the granular permission. - **Roles**: role list assigned to that granular permission. - **Description**: role description - **Information system**: asset or application, from a functional point of view. - **Target system**: target system name. - **Domain**: the role is limited to that scope. ## Actions #### Authorization query action| **Import** | Allows you to upload a CSV file with the authorization data to add or to update the granular control system. If they exist, the values of the CSV file will prevail. First, you need to pick up a CSV file, that CSV has to contain a specific configuration. Then you need to check the contents. And finally, you need to select the mappings for each column of the CSV file to import the data correctly and to click the Import button. |
| **Download CSV file** | Allows you to download a CSV file with the authorization data. |
| **Add new** | Allows you to add a new role to the authorization. You can choose that option clicking the add button (+). First, you need to search a role writing the role name on the field, and Soffid will show the values related. Second, you can select one or more roles and accept. And finally, you need to apply changes to save the roles added. If you cancel that action, no role will be assigned. |
| **Delete** | Allows you to delete one or more roles from an authorization. To delete one role, you need to click the subtraction symbol (-), located at the end of the row, of the role which you want to delete and then apply changes. To delete more than one role, you can select the roles which you want to delete and there click the subtraction symbol (-) and then apply changes. It is mandatory apply changes to save the roles deleted. Soffid will ask you for confirmation to perform that action, you could confirm or cancel the operation. |
| **Apply changes** | Allows you to update the changes made on the authorization. |
| **Undo** | Allows you to quit without applying any changes. |
Once you check the **Enforce TLS connections to Soffid Console** option, there are no easy way to come back. You should use this option only en Production environments.
Not all the external systems are included, only the ones that have marked the check "Trust password" on the agent. For more information about agents please visit the [Agents](https://bookstack.soffid.com/books/soffid-3-reference-guide/page/agents "Agents") page.
Once an agent is configured, Soffid will still use its internal tables to authenticate usernames and passwords. If the password entered by the user does not match, the Soffid core will issue a "ValidatePassword" task for each trusted target system. If any of the trusted target systems accepts the password, it will be hashed and stored in Soffid tables and login will be accepted. ### External SAML identity provider It should be noted this feature does not depend on the federation addon. That is a feature included by default in the Soffid smart engine to allow you to include in the authentication flow a mechanism to use a third-party SAML system. - **Enable**: check it (select value Yes) to use an external SAML Identity Provider. - **Soffid Server host name**: the URL that will be used by external IdP. This URL will be resolved by end user's browser in order to send the SAML assertion. - **SAML federation metadata**: the URL where federation information can be found. If the Soffid console can fetch federation metadata, the Identity provider drop-down will be filled in with any identity provider found in the federation metadata URL. - **Cache limit (seconds)**: how often the federation information will be refreshed. By default, 10 minutes will be taken. - **Identity provider**: Identity Provider to use for authentication. Finally, download the Soffid Console and load it into your SAML Identity Provider federation. If SAML Identity Provider is enabled, as well as username and password, the user will have the chance to select the preferred authentication method. Otherwise, if only SAML is enabled, the user will be automatically redirected to SAML Identity Provider.Bear in mind that the Identity Provider needs to have enabled the OpenID profile.
Also, the Identity Provider cert must be in the Console cacerts.
If you want to configure the **Soffid OTP** you could visit [Two factor authentication (2FA)](https://bookstack.soffid.com/books/two-factor-authentication-2fa-VsJ "Two factor authentication (2FA)") chapter.
### Second Factor Authentication configuration - **Pages that optionally require OTP authentication for users with an enabled token**: (Optional) If a URL optionally requires OTP authentication, and the user does not have any OTP token, access will be granted. Otherwise, if the user has an OTP token, the OTP value will be required, and no access will be allowed until the user provides the right token value. - You can include the list of pages to include the two factors only for the users with the token.| **Download metada** | Allows you to download an XML file with metadata to load it into your SAML Identity Provider federation when you use an External SAML identity provider |
| **Confirm changes** | Allows you to save the changes made in the Authentication setup. |
| **Add new domain** | Allows you to create a new **password domain**. You can choose that option on the hamburger menu or click the add button (+).To add a new password domain it will be mandatory to fill in the required fields |
| **Add new password policy** | Allows you to create a new **password policy** on a specific password domain. Below the father password domain, you can find the button to perform that action. To add a new password policy it will be mandatory to fill in the required fields. |
| **Apply changes** | Allows you to save a new password domain or to update the password domain changes. To save the data it will be mandatory to fill in the required fields. |
| **Delete** | Allows you to delete a password domain. To delete a password domain you can click on the hamburger icon and then click the delete button (trash icon). Soffid will ask you for confirmation to perform that action, you could confirm or cancel the operation. |
| **Undo** | Allows you to quit without applying any changes. |
| **Apply changes** | Allows you to create a new password policy or to update password policy changes. To save the data it will be mandatory to fill in the required fields. |
| **Delete** | Allows you to delete a password policy. To delete a password policy you can click on the hamburger icon and then click the delete button (trash icon). Soffid will ask you for confirmation to perform that action, you could confirm or cancel the operation. |
| **Undo** | Allows you to quit without applying any changes. |
| **Add word** | Allows you to create a new forbidden word. Those forbidden words may not be used to create a password if they are selected. |
| **Add new** | Allows you to add a new certificate. You can choose that option on the hamburger menu or click the add button (+). To add a new certificate it will be mandatory to fill in the required fields. |
| **Delete** | Allows you to remove one or more certificates by selecting one or more records and next clicking the button with the subtraction symbol (-). To perform that action, Soffid will ask you for confirmation, you could confirm or cancel the operation. |
| **Download CSV file** | Allows you to download a CSV file with the digital certificates data. |
| **Next** | Allows you to browse the wizard to create a new certificate. |
| **Apply changes** | Allows you to save the data of a new certificate or to update the data of a specific certificate. To save the data it will be mandatory to fill in the required fields |
| **Undo** | Allows you to quit without applying any changes. |
| **Issue Type** | **Description** |
| account-created | This issue is created when the Sync Server detects when a new account is created. This may occur after the Reconciliation process has been executed. |
| disconnected-system | This issue is created when the Sync Server detects that some target system is offline. |
| discovered-host | This issue is created when the Sync Server detects a new host in the network. This only occurs after the Network Discovery process has been executed. |
| discovered-system | This issue is created when the Sync Server detects a new system in a host. This only occurs after the Network Discovery process has been executed. |
| duplicated-user | This issue is created the system detects that there are duplicate users, or when the task is generated manually from the user management. |
| enabled-account-on-disabled-user | This issue is created when an enabled account is detected on a disabled user. This may occur after the reconciliation process has been executed. |
| failed-job | This issue is created when the system detects job failures. This may occur by running any scheduled task. |
| global-failed-login | This issue is created when the number of session start failures exceeds the threshold of 0.8. |
| integration-errors | This issue is created when the Sync Server detects an integration error between Soffid and an end system. You can check the task in the Monitoring & Reporting. |
| locked-account | This issue is created when an account has been blocked for exceeding the maximum number of login attempts. You can configure the property *Lock after failures* in the Password policies settings. Even if it is temporarily locked, the incident will be generated. |
| login-different-country | This issue is created when Soffid detects a new login from a different country. It only works with the Identity Provider and it is necessary to have the geolocation database updated. |
| login-from-new-device | This issue is created when Soffid detects a new login from a new device. It only works with the Identity Provider. |
| login-not-recognized | This issue is created when Soffid detects a login not recognized (disabled user or user does not exist) in the Soffid Console or in Soffid as an Identity Provider. |
| otp-failures | This issue is created when an OTP is blocked for exceeding the number of attempts. Currently blocked with 10 unsuccessful attempts. |
| pam-violation | This issue is created when any of the rules of the PAM are violated. You can define the PAM rules and the PAM policies. Be in mind, that you must check the "Open issue" option in the PAM policies you wish to control. |
| password-changed | This issue is created when a Password change is detected. These changes come from the end system (Active Directory or Soffid OpenLDAP) and Soffid has been notified. The issue is not created if it is the operator or a script that changes the password in Soffid. |
| permissions-granted | This issue is created when it is detected that permissions have been given to a user on the end system. This may occur after the reconciliation process has been executed. |
| risk-increase | This issue is created when it is detected the risk level of a user is increased. You can configure the risks in the Segregation of Duties option. |
| robot-login | This issue is created when it is detected is detected that someone who has not passed the CAPTCHA is trying to log in to the Identity Provider. |
| security-exception | This issue is created when unauthorized access to the console via WebService or admin console occurs. |
Note that it will be necessary to restart the Sync Server when changing the action of an issue.
## Actions #### Issue policies query action| **Download CSV file** | Allows you to download a CSV file with the issue policies data. |
| **Add new** | Allows you to add a new action to the issue policy. You can choose the action from the action list. Depending on the selected action, you must fill in different information. Once the information will be filled in, you need to close the window and Apply the changes. |
| **Delete** | Allows you to delete one or more actions from the actions list. |
| **Apply changes** | Allows you to update the changes made to the issue policy. |
| **Undo** | Allows you to quit without applying any changes. |
For more information you can visit [the Break Glass book](https://bookstack.soffid.com/books/break-glass).
## Screen overview [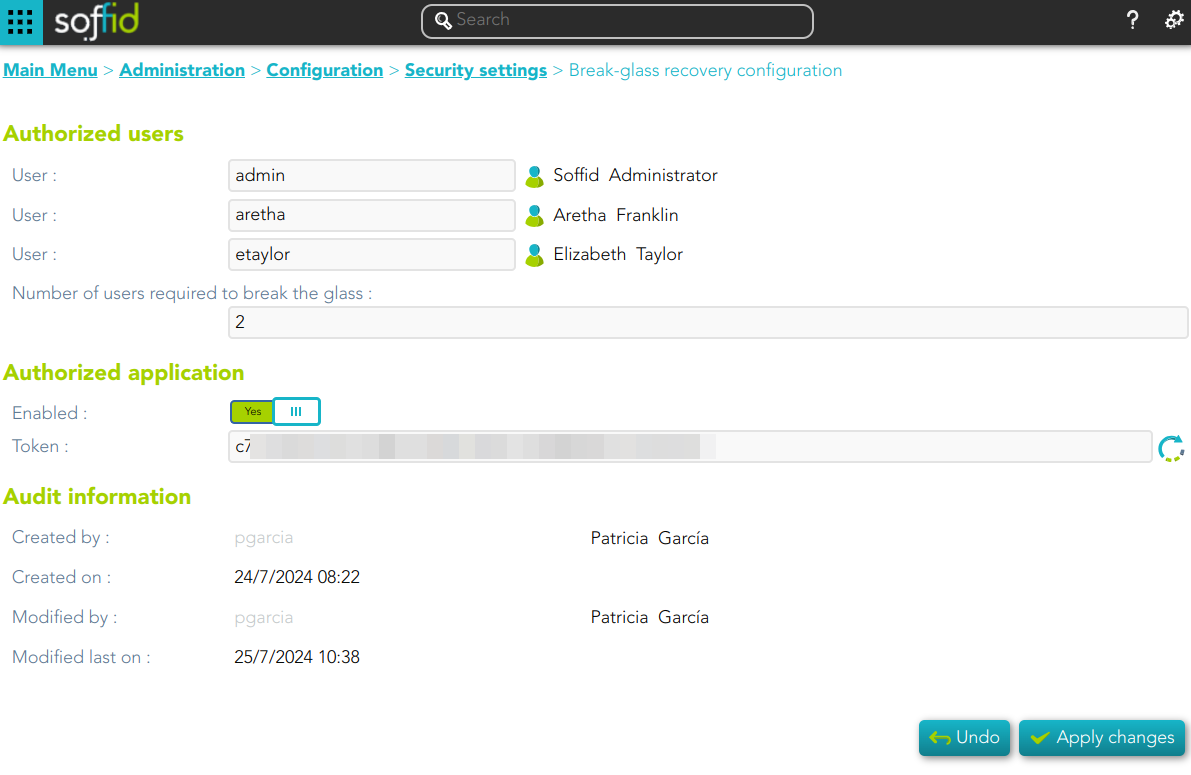](https://bookstack.soffid.com/uploads/images/gallery/2024-07/image-1721911781264.png) ## Related objects 1. **[User](https://bookstack.soffid.com/books/soffid-3-reference-guide/page/users)** ## Standard attributes #### Authorized users Allows you to configure from one to three users to break glass - **User**: allows you to choose the first users to break the glass. - **User**: allows you to choose the second users to break the glass. - **User**: allows you to choose the third users to break the glass. - **Number of users required to break the glass**: this number allows you to configure the number of users required to break the glass #### Authorized application - **Enabled**: allows you to enable or disable the the break-glass recovery. - **Token**: allows you to generate a new token by clicking the refresh icon. #### Audit information - **Created by** - **Created on** - **Modified by** - **Modified last on** ## Actions| **Generate Token** | Allows you to generate a new Token by clicking the refresh icon [](https://bookstack.soffid.com/uploads/images/gallery/2024-07/image-1721911436603.png) |
| **Apply changes** | Allows you to update the changes made on the break glass recovery configuration. |
| **Undo** | Allows you to quit without applying any changes. |