If your system is not in the previous list, it's possible to include it easily! For more information to check if your system may be synchronized with this connector you do not hesitate to contact us through our [Contact form](http://www.soffid.com/contactform/)
### Prerequisites It is needed a user with full administrator access. ## Download and Install This addon is located in the Connectors section and its name is **LDAP plugin.**For more information about the installation process you can visit the [Addons Getting started](https://bookstack.soffid.com/books/addons-getting-started/page/getting-started "Addons installation") page.
## Agent Configuration ### Basic #### Generic parameters After the installation of the addon, you may create and configure agent instances. To configure this LDAP Connector you must select "LDAP-Custom (with triggers)" in the attribute "Type" of the generic parameters section in the agent's page configuration.For more information about how you may configure the generic parameters of the agent, see the following link: [Agents configuration](https://bookstack.soffid.com/books/soffid-3-reference-guide/page/agents "Agents")
[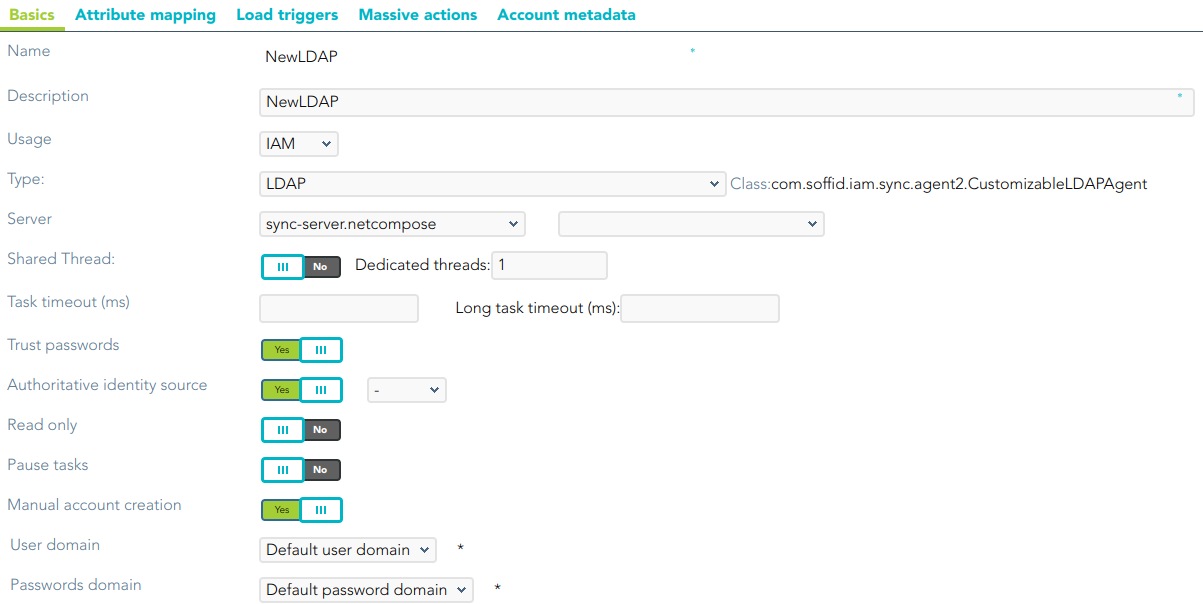](https://bookstack.soffid.com/uploads/images/gallery/2024-05/image-1715077578477.png) #### Custom parameters Below there are the specific parameters for this agent implementation:| **Parameter** | **Description** |
|---|---|
| User name | User name in DN format, including base name if needed |
| Password | Password |
| Host name | Host name of the server |
| Enable SSL | |
| Base DN | LDAP Base name |
| PasswordAttribute | |
| Password hash algorithm | The algorithm is used to encrypt the password. For instance SHA-1, SHA-256, MD5, etc |
| Password hash prefix | |
| LDAP Query page size | |
| Enable debug | Two options: Yes, No. When it is enabled more log traces are printed in the Synchronization Server log |
As a limitation, it cannot detect password changes to be propagated to other systems.
#### Properties Some agents require to configure some custom attributes, you will use the properties section to do that.**Property** | **Value** |
|---|---|
| rename | true |
| key | LDAP attribute where Soffid account name is stored. If the property is not present, object will be searched by its distinguishedName |
| modificationTimestamp | LDAP attribute |
| removeDisabledAccounts | Set to true to remove disabled accounts from LDAP server |
**Property** | **Value** |
|---|---|
| rename | true |
**System attribute** | **Value** |
|---|---|
| objectClass | LDAP Object Class. It can evaluate to an array of objects |
| dn | Full qualified object name |
For more information about how you may configure attribute mapping, see the following link: [Soffid Attribute Mapping Reference](https://bookstack.soffid.com/link/72#bkmrk-soffid-attributes)
For instance: [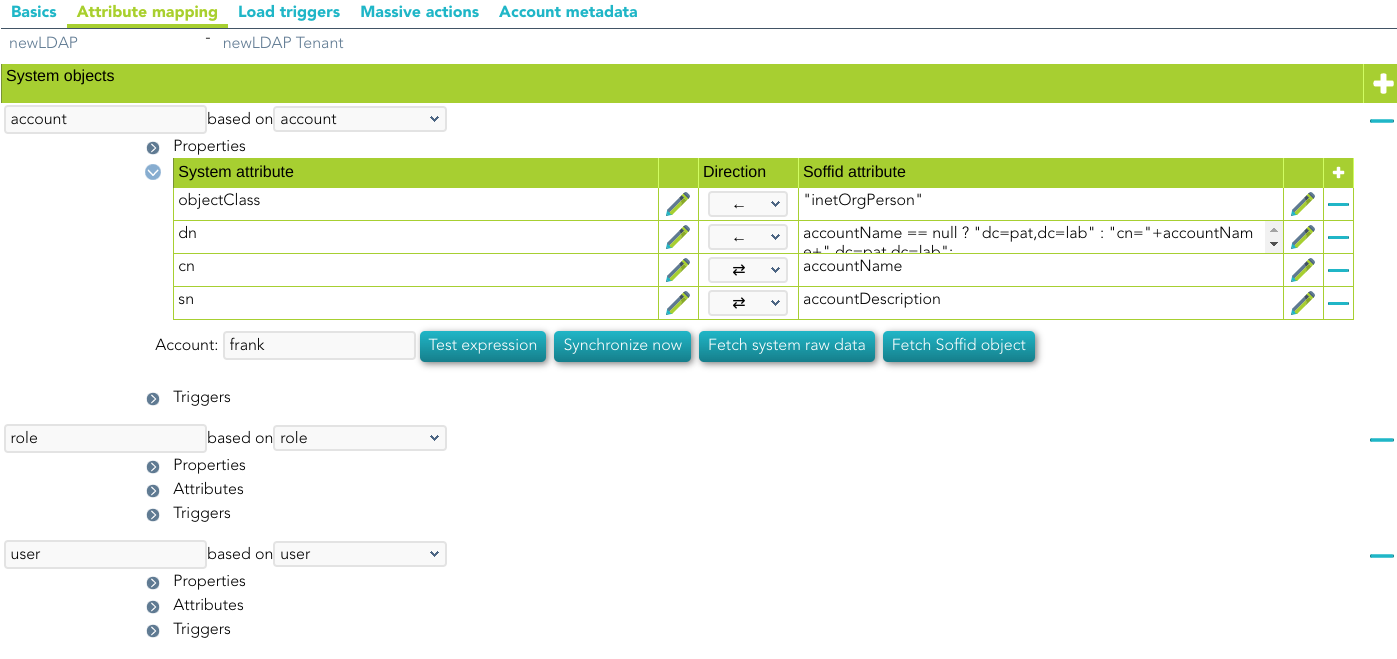](https://bookstack.soffid.com/uploads/images/gallery/2022-07/image-1659087931478.png) #### Triggers You can define BeanShell scripts that will be triggered when data is loaded into the target system (outgoing triggers). The trigger result will be a boolean value, true to continue or false to stop. Triggers can be used to validate or perform a specific action just before performing an operation or just after performing an operation on target objects.To view some examples, visit the [Outgoing triggers examples page](https://bookstack.soffid.com/books/connectors/page/outgoing-triggers-examples "Outgoing triggers examples").